Detect the Most Common Ransomware TTPs to Prevent Attacks
Forescout Vedere Labs does a deep dive and prescribes mitigation.
Originally published March 22, 2023
The recent high-profile cyberattack on MGM Resorts International, still under investigation, put ransomware back in the public spotlight. News reports and social media posts cited widespread issues with deactivated digital room keys locking guests out of their rooms; slot machines, ATMs and elevators taken offline; and websites taken down. Over a dozen MGM hotels and casinos reportedly had to shut down operations for 10 days. This time, what happened in Vegas didn’t stay in Vegas.
The thought of inoperable gaming machines may send chills down some gamblers’ spines, but it’s the breadth of the attack, which impacted the computer systems at all MGM properties across the country and exposed the personal data of 10.6 million guests, that gave the cybersecurity community pause. A group of hackers known as Scattered Spider effected the breach, using software and attack tools provided by the larger ransomware-as-a-service group known as ALPHV. The Gen-Z attackers, mostly 17 to 22 years old, are known to be skilled at social engineering and bypassing multi-factor authentication.
Casino breaches are sure to make headlines, but the takeaway here is you must be ever vigilant in the face of less notorious ransomware attacks that occur every day. Read our recent threat briefing on how to detect the most common ransomware TTPs – so you can prevent attacks.
In our new threat briefing, Forescout Research – Vedere Labs details tactics, techniques and procedures (TTPs) commonly adopted by ransomware groups and provides specific mitigation recommendations. In addition to basic cyber hygiene practices, we recommend using Forescout Threat Detection & Response for extended detection and response. Its 1,500+ detection rules cover hundreds of the TTPs most commonly used by ransomware.
The increasing sophistication of attacks, coupled with a growing number of threat actors makes ransomware one of the most dangerous cyber threats nowadays. Ransomware attacks can lead to data loss, disrupt business operations and compromise sensitive information, causing significant financial losses and reputational damage that can be devastating to individuals and organizations.
Open-source tracking of close to 100 ransomware groups indicates an average of 231 breaches per month between September 2022 and February 2023, with the top three groups alone executing 157 attacks in the past 30 days (February 15 to March 15). At the same time, the FBI’s recently released 2022 Internet Crime Report revealed ransomware breaches last year of 2,385 organizations, including 860 in critical infrastructure sectors. Healthcare was the most impacted sector with 210 breaches, followed by manufacturing (157) and government (115). The top three groups active in these sectors were LockBit (149 breaches), ALPHV (114) and Hive (which was recently disrupted, but had 87 breaches last year).
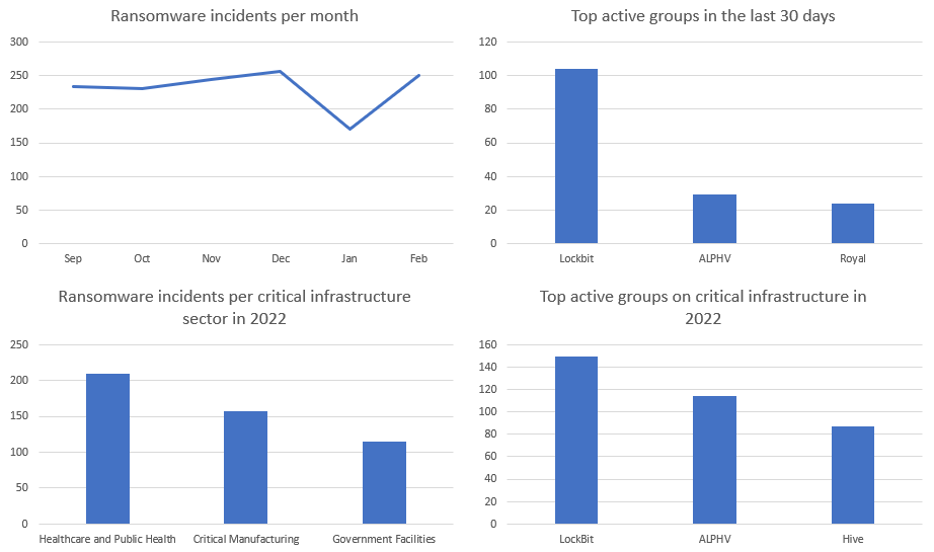
Sources: Top two charts contain data from https://darkfeed.io. Bottom two charts: https://www.ic3.gov/Media/PDF/AnnualReport/2022_IC3Report.pdf
Double extortion, targeted attacks and zero-day exploits
These raw statistics hide the fact that ransomware has been evolving rapidly, especially since 2020, with the following changes:
- The use of double extortion, which involves not only encrypting the victim’s files but also stealing data and threatening to publish it unless the ransom is paid. The pressure on victims has been continually increasing. In 2023, groups such as ALPHV and Medusa started releasing pictures of patients getting cancer treatments and leaked student records to shame victim organizations into paying.
- The increased focus on targeted attacks against specific organizations rather than casting a wide net. These attacks are often conducted after extensive reconnaissance and can be much more successful in terms of both encrypting data and obtaining payment.
- The use of zero-day exploits, which have no patch available and are harder to detect and defend against, in attack campaigns. Recent examples include a zero-day used to circumvent Windows SmartScreen and deploy the Magniber ransomware and a zero-day in the Fortra GoAnywhere MFT secure file-sharing solution used by Clop to exfiltrate data.
Although ransomware groups continue to evolve and refine their operations, the more things change, the more they remain the same. In 2022 the most commonly used TTPs remained mostly constant.
Forescout Vedere Labs has been consistently analyzing and reporting on ransomware payloads, incidents and behaviors, such as the rise in Linux and ESXi targets, for the past few years. In this new report, we revisited those analyses and focused on campaigns observed in the past year to determine the TTPs commonly used by ransomware adversaries. We categorized each observed TTP using the MITRE ATT&CK framework. Families analyzed include the top three currently active (LockBit, ALPHV and Royal) as well as past operations such as Ryuk, REvil, Conti and Hive.
Common ransomware TTPs
The table below summarizes the common TTPs we observed.
Mitigation recommendations that rely on basic cyber hygiene
Our analysis indicates that adversaries often follow similar patterns in their attacks. This provides an opportunity to systematize recommendations to prevent and detect them. However, it’s important to note that the TTPs in this report are just the most common examples. It is critical for organizations to implement strong security practices and stay vigilant against the evolving nature of cyber threats.
Basic cyber hygiene recommendations are still effective against ransomware. They include identifying and patching vulnerable devices in your network, segmenting the network to avoid spreading an infection and monitoring network traffic to detect signs of intrusion, lateral movement or payload execution. These recommendations are detailed on CISA’s Stop Ransomware project page, especially their ransomware guide.
For those who have been victims of a ransomware attack, the ID Ransomware project helps identify the specific family used, while the No More Ransom project links to dozens of publicly available decryptors.
Beyond these general recommendations, two sets of specific mitigations can be derived from this report:
- All the example commands shown throughout the document can be used for threat detection and threat hunting. It’s worth noting that many of those commands, such as remote administration, are not inherently malicious and could also be used for legitimate purposes. Therefore, correlating individual events with signals from multiple sources, such as EDR and network monitoring, is paramount.
- The table below summarizes specific prevention and detection actions for the common tactics analyzed in this report.
| Technique | Recommendations |
|---|---|
| Initial Access |
|
| Persistence |
|
| Discovery |
|
| Lateral movement |
|
| Exfiltration |
|
How Forescout can help
Forescout Threat Detection & Response collects telemetry and logs from a wide range of sources such as security tools, applications, infrastructure, cloud and other enrichment sources, correlates attack signals to generate high-fidelity threats for analyst investigation and enables automated response actions across the enterprise.
Forescout TDR has more than 1 detection rules, covering 196 MITRE ATT&CK techniques. Not by accident, the techniques with the most associated rules are all commonly used by ransomware, such as User Execution (T1204) with 148 rules, Valid Accounts (T1078 – which is commonly used to access External Remote Services) with 124 rules and Phishing (T1566) with 115 rules.
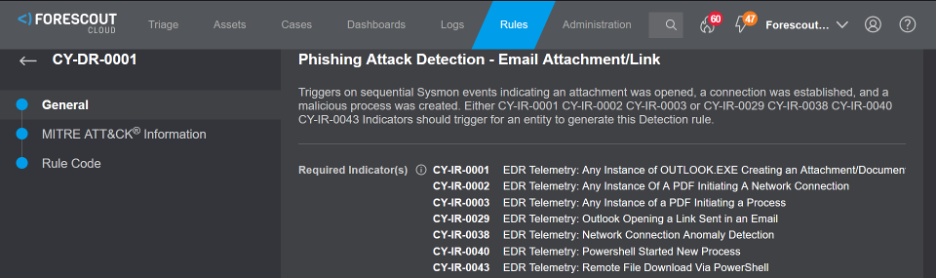
The figure below shows a description of the “Phishing Attack Detection – Email Attachment/Link” detection rule, which triggers when sequential Sysmon events indicate that an attachment was opened, a connection was established and malicious process was created.