Reducing OT Network Downtime and Risk: Lessons Learned from the Norsk Hydro Cyberattack
At the end of March, the cybersecurity news wires lit up with stories about how Norsk Hydro, a Norwegian-based company with global operations and one of the largest aluminum producers in the world, had become the victim of a cyberattack 1. Norsk Hydro recently stated that the incident will likely cost them up to $52 million in the first quarter of 2019 and have even had to postpone their Q1 earnings report by five weeks to June 5 from April 30 2.
There are a couple of important things to point out about the impact of this event.
The first is that, because cyber incidents can easily spread between business units and impact an entire worldwide organization, their financial impact can be extensive. Proving, yet again, that everyone within an organization is increasingly a cybersecurity stakeholder.
Secondly, the Norsk Hydro incident was notable in the fact that it was an IT-centric event that impacted OT operations. The operational floor was able to switch to manual mode, but they depend on things like sales orders and planning documents that traditionally rely on IT systems to know what and how much to produce. The interdependence of IT and OT systems on each other to function at maximum efficiency is the new reality for most companies.
The Norsk Hydro incident is an unfortunate illustration of how increasing cyber risk to OT networks from their exposure to IT systems can result in severe financial pain. To mitigate potential financial losses, organizations need to adopt a fresh perspective on their cybersecurity strategy, which should includean enterprise-wide security posture incorporating both IT and OT.
In this post, we will focus specifically on what OT asset owners should do to really gain control and reduce risk. The first step is always real-time, in-depth ICS network visibility.
Specifically, asset owners need to know:
- Which assets have access to the OT network
- Where and how cybersecurity policies and best practices are being applied to these assets
- How rapidly operational and compliance data can be documented
- Whether installed ICS cybersecurity technology can assist with and automate threat response
Once they can answer these visibility-related questions, they can begin to develop a comprehensive risk management strategy for the OT network. Now that we understand what they need to know, let’s focus on how to collect this information.
There are four important steps that should be taken to implementan effective risk management strategy for OT networks. These include:
- Assess– Establish complete OT asset inventory
- Secure– Segment assets and create an ICS network baseline
- Monitor– Continuously monitor the network and quickly turn IoCs into actionable intelligence
- Respond– Establish proper RACI matrix to share the right info with the right people
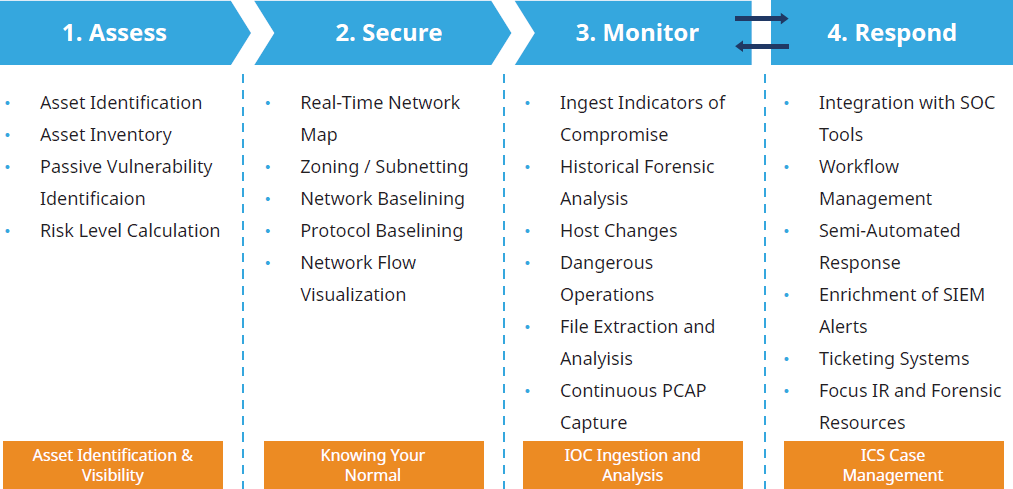
Deploying a technology that can continuously and non-intrusively discover, classify and monitor network devices is a great way to implement these four steps and help keep OT networks safe from cyber adversaries. Because OT attacks typically originate in the IT environment, like the one targeting Norsk Hydro, it’s important to choose a solution that is effective in both IT and OT environments for a holistic view of threats to the entire enterprise 3. The technology should also quickly and easily integrate with other IT-based security solutions, such as SIEMs and firewall applications.
After witnessing the severe financial loss suffered by Norsk Hydro, critical infrastructure cybersecurity stakeholders all over the world should strongly consider adopting a cyber defense methodology like this one and implementing an OT network visibility and cybersecurity solution.
To take a deep dive into how you can implement this four-step approach and the potential ROI it can help provide, download this white paper
1 Cyber Is Becoming Physical: Ransomware Attack Hits Aluminum Producer Norsk Hydro, Forescout, by Brandon Workentin
2 Norsk Hydro expects cyber attack costs of up to $52 mln in Q1, Reuters
3 7 Questions Every Security and Risk Management Leader Should Ask When Choosing an OT Security Solution, Forescout, by Colby Proffitt
