Ransomware Trends: Understanding the Payment Ban Debate
Ransomware has become the scourge of the cybersecurity world. Look at the impact: organizations paid $1.25 billion in 2023 and $800 million in 2024 in crypto-based ransomware payments.
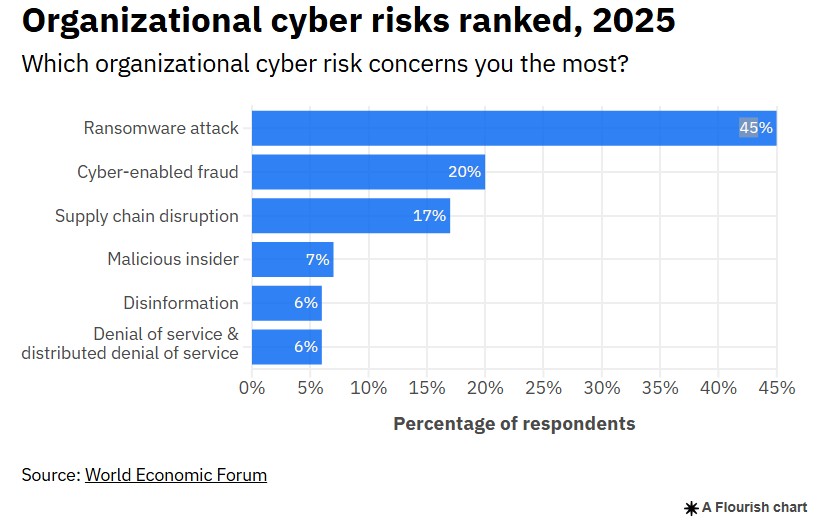
CEOs and CSOs now rank ransomware as their top cyber risk in 2025.
The World Economic Forum confirms ransomware remains the top organizational cyber risk year over year. Forty-five percent of CEO/CSO respondents rank it as their primary concern—more than double the second-highest threat (cyber fraud).
The UK’s National Cyber Security Centre sees no signs of attacks slowing:
“Leaders at the Annual Meeting on Cybersecurity 2024 expect significant innovations in ransomware attacks. The continued adoption of Ransomware-as-a-Service (RaaS) entrenches the commoditization of the ransomware model.”
Organized Crime Scales Through Ransomware-as-a-Service
Traditional organized crime groups have entered the cybercrime arena, transforming its character.
“Organized crime groups cause physical harm and show less concern about attacking critical social services like hospitals,” the WEF explains.
This cultural shift, combined with Ransomware-as-a-Service (RaaS) scaling, widens the pool of potential victims. RaaS and advanced social engineering methods “enable threat actors to outpace traditional defenses.”
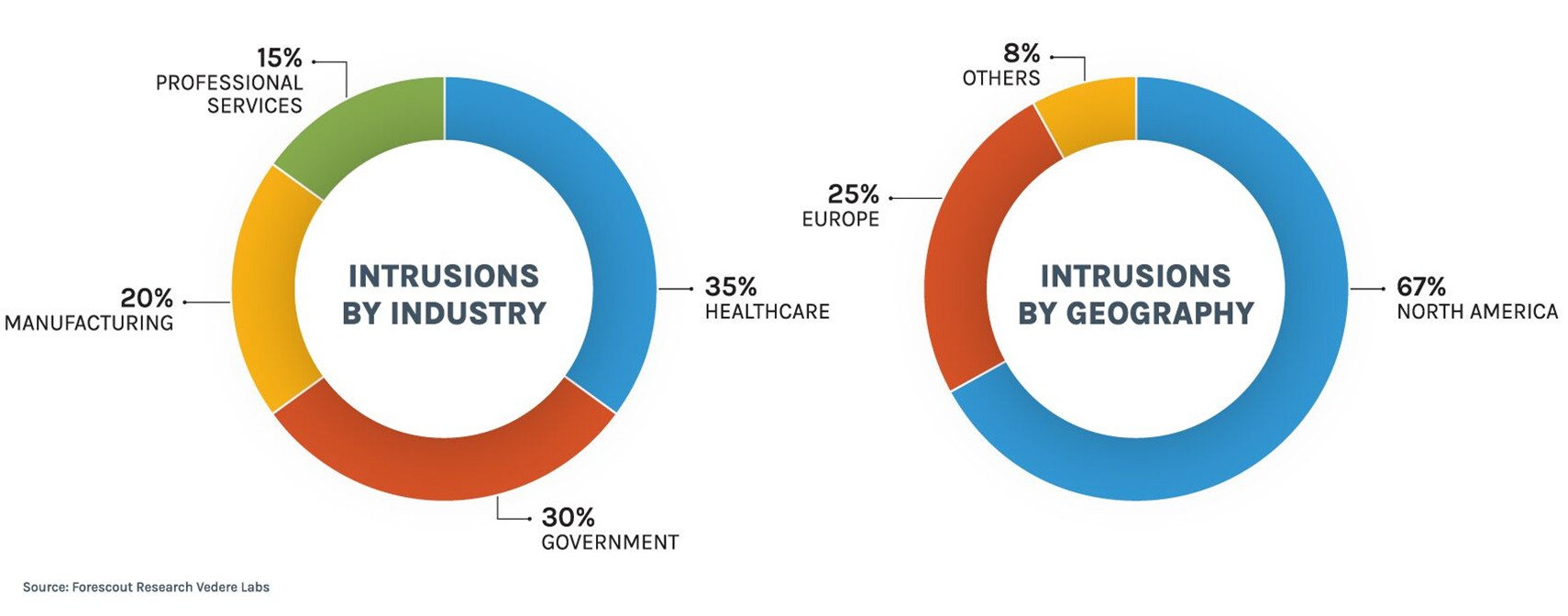
Virtually any criminal group can now scale attacks via RaaS, broadening the threat landscape. Forescout Vedere Labs’ 2025H1 Threat Review report analyzes Interlock ransomware, which evolved from an unknown entity into an emergency-level threat within one year. Interlock claimed over 50 victims in 2025 alone across healthcare, government, and manufacturing sectors—industries that maximize ransom payment leverage through “big game hunting.”
New Policy: The UK Wants to Ban Ransom Payments
The UK government plans to ban public sector organizations (and some private ones) from paying ransoms to cybercriminals. No federal government worldwide has ever issued an outright ban, though most strongly advise against payments.
The rationale: lower incentives for attackers while protecting critical public services and infrastructure. The ban targets public sector and critical national infrastructure (CNI) organizations—schools, hospitals, healthcare providers, transportation, energy, and telecom. All public/CNI organizations will face audits and penalties for non-compliance.
Private UK Organizations Face Restrictions Too
Businesses not covered by the ban must notify the government before paying ransoms. The government will offer advice and support, including warnings that payments to sanctioned cybercriminal groups risk breaking the law.
Why Now?
Ransomware hit numerous UK public services in the past year, including local councils and hospitals.
“Ransomware puts the public at risk, wrecks livelihoods, and threatens essential services,” said UK Security Minister Dan Jarvis. “We’re determined to smash the cybercriminal business model and protect the services we rely on.”
Jarvis echoes ban supporters who argue extortion payments fuel the ransomware model, incentivizing continued attacks.
Go deeper: Watch our experts, Rik Ferguson, VP of Security Intelligence and Alison King, VP of Government Affairs, discuss ransomware, including the payment bans in the UK.
Six Major Criticisms of the Ransom Payment Ban
Critics highlight how difficult making the ban fair and effective would be, warning of unintended consequences:
- Business viability: Companies may need more expensive recovery routes, risking their survival. Skepticism runs high that government will bail them out.
- Unequal consequences: International companies could circumvent UK regulators by paying from foreign accounts, disadvantaging smaller UK firms that comply.
- Inaccurate reporting: Some companies may pay ransoms without reporting attacks or mislabel them. This harms the security community’s ability to gather intelligence on threats, techniques, and patterns.
- Double extortion: Companies that secretly pay face potential re-extortion, with criminals threatening to expose unreported payments to regulators.
- Target shifting: Attackers could target individuals instead of banned businesses, putting business leaders, politicians, and high-net-worth individuals at risk.
- Higher insurance premiums: Companies choosing expensive recovery over ransom payments will pass costs to insurers, raising ransomware insurance rates.
The US Rejects Payment Bans
Though the FBI, NSA, and CISA advise against ransomware payments, former CISA Director Jen Easterly doubts the US will ban them.
“From a practical perspective within our US system, I don’t see it happening,” said Easterly at the Oxford Cyber Forum.
The Institute for Security and Technology’s Ransomware Task Force also opposes bans, according to Cybersecurity Dive:
“While a ban may be easier policy than driving preparedness, it will almost certainly create the wrong impact. Organizations making payments are declining, suggesting we’re on the right path.”
Are Payments Just Business Costs in the US?
Most ransom payments are already tax-deductible federally and in 48 states. If payments constitute capitulation to criminals, why allow tax deductions?
Tax experts say businesses can deduct ransomware payments as “ordinary and necessary” expenses or “theft losses” (if insurance doesn’t compensate). Restrictions: payments cannot go to sanctioned entities or violate federal law. Only two states ban payments (North Carolina and Florida)—and only for government agencies, not businesses.
U.S. agencies unanimously view payment bans as capitulation or admission of defeat. They prefer building business resilience against cyber attacks.
“Most organizations lack cyber resilience and remain woefully underprepared for ransomware,” RTF co-chairs told Cybersecurity Dive. “A ransom payment ban won’t change that. Attackers will continue launching attacks knowing organizations lack sufficient defenses.”
North Carolina implemented a ban, yet it did nothing to slow ransomware attacks statewide.
Progress continues without bans. CISA’s proposed rule for the Cyber Incident Reporting for Critical Infrastructure Act of 2022 will compel over 300,000 US critical infrastructure owners, operators, and suppliers to quickly report attacks and ransom payments starting in 2026. US organizations already cannot pay ransoms to individuals or entities sanctioned by the US Department of Treasury’s Office of Foreign Assets Control.
Cyber Insurance Coverage Varies Widely
Many cyber insurance policies cover ransom payments, but coverage varies dramatically. Some cover ransoms plus negotiation fees, data recovery, remediation, and legal expenses. Others exclude ransom payments entirely.
Typical Coverage (with proper cybersecurity measures in place):
Data restoration and recovery: Covers retrieving or recreating lost, corrupted, or stolen data. Some policies cover ransomware payments for data recovery, though authorities advise against it and providers increasingly limit this coverage.
System damage repair: Covers repairing or restoring computer systems and software damaged by attacks.
Hardware replacement: Specialized policies cover replacing “bricked” hardware when more cost-effective than repairs. Not standard; doesn’t cover physical damage unrelated to cyberattacks.
What Insurance Typically Excludes:
- Preventative measures: Security architecture improvements, patching, or hardening are operational expenses, not covered.
- “Betterment” coverage: Optional add-on pays for post-breach improvements to eliminate vulnerabilities.
- Existing flaws: Insurers may deny claims from exploiting known, unfixed vulnerabilities. Companies need minimum cybersecurity levels to qualify.
To obtain ransomware coverage, organizations typically must have multi-factor authentication, data encryption, endpoint detection and response systems, vulnerability patching, and network segmentation.
Insurance Doesn’t Guarantee Survival
In 2023, UK transport company KNP complied with industry standards and had $1 million ransomware coverage. Hacker group Akira demanded far more and refused to release business data. The 158-year-old company went bankrupt and laid off all workers.
KNP represents many small and medium businesses (SMBs). According to a recent study from Accenture, 43% of cyberattacks target SMBs, yet only 14% prepare adequately to defend themselves.
The HIPAA Journal identifies mid-sized companies as the sweet spot for hackers—they invest less in cybersecurity than large companies but have revenue for substantial ransoms. In Q4 2023, the average victim company had 231 employees.
Proactive Steps Before Ransomware Strikes
Practice Basic Cyber Hygiene
- Use complex, unique passwords and implement MFA across all systems
- Patch all systems, tools, and infrastructure against known vulnerabilities
- Apply zero-trust principles—employees access only systems their roles require
Invest in Cybersecurity Infrastructure
- Deploy advanced antivirus and anti-malware solutions across all devices
- Segment networks and systems—isolate critical systems so breaches don’t compromise entire networks
- Maintain encrypted, offline backups with workable recovery plans
- Or partner with cybersecurity service providers offering these solutions
Train and Educate Staff
- Train employees on phishing, social engineering, and suspicious activity
- Perform regular penetration tests and phishing simulations
Develop a Ransomware Response Plan
- Outline clear steps for detection, containment, communication, and recovery
Audit and Certify
- Conduct regular third-party assessments to identify gaps
Collaborate and Report
- Join industry groups or government initiatives including NCSC’s Early Warning service
- Register for threat intelligence feeds like Forescout’s Vedere Labs
- Report incidents to help authorities track threats
Review Cyber Insurance
- Ensure policies cover ransomware, business interruption, mitigation, remediation, and data recovery
- Understand limitations, exclusions, and payout triggers
How Forescout Can Help
The Forescout 4D Platform™ enables you to see and understand what’s on your network and where vulnerabilities exist. Our threat intelligence combined with our 4D Platform provides baseline capabilities to better manage cyber attacks.