PrintNightmare
The Infamous Windows Print Spooler Service Hit Again
During June’s 2021 Patch Tuesday, Microsoft addressed a minor local privilege escalation (LPE) vulnerability (CVE-2021-1675) in the Windows Print Spooler service (spoolsv.exe), which is responsible for printing management in Windows.
Almost two weeks later, the vulnerability impact was changed from LPE to Remote Code Execution (RCE) after researchers found that although the official fix was deployed, the operating system was still exposed to an RCE running in the context of the SYSTEM privileges by exploiting the Spooler service. Microsoft is tracking this weakness under CVE-2021-34527.
This vulnerability was dubbed PrintNightmare because the Spooler print service fails to restrict access to the functionality that allows users to add printers and related drivers. As a result, it can allow any remote or local authenticated actor to run arbitrary code with SYSTEM privileges. This is not the first time the Print Spooler service is associated with Windows attack. PrintSpoofer, for example, leverages the Print Spooler service to get a SYSTEM token and run custom commands.
Microsoft released an unusual out-of-band patch to address PrintNightmare’s remote code execution (RCE) vulnerability. Yet, researchers demonstrated the patch fails to fully fix PrintNightmare RCE vulnerability in certain scenarios. On top of that, CISA encouraged administrators to disable the Spooler services in Domain Controllers and other critical systems that do not need to print, as suggested by Microsoft’s how-to guide.
Exploitation
To successfully exploit CVE-2021-34527, any local or remote attacker must be authenticated (low privileged) in advance. Next, an attacker could get full control of the organizational Active Directory by targeting a vulnerable Spooler service running on the Domain Controller and then run arbitrary code with the highest SYSTEM privileges.
Many proof-of-concept exploits have already been published for this vulnerability.
Detection and Solution
In response to this critical issue, Microsoft released expanded patches. Still, they turned out to be bypassed under certain scenarios, leaving affected assets exposed even after successful patching.
Microsoft shortly released an update to the patch advisory where it clarifies that for the patch to be effective, the following registry configuration must be set to 0 or not exist at all (default):
- HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
- HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint\NoWarningNoElevationOnInstall
- HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint\UpdatePromptSettings
Forescout has released a Security Policy Template to detect devices running vulnerable Windows operating systems, according to the latest guidance determined by Microsoft.
Analysis
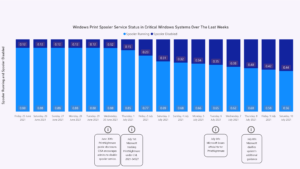
Using the Forescout Device Cloud, Forescout researchers have evaluated the status of the infamous spooler service (i.e., whether the service is up and running or disabled down) on critical Windows systems, such as Domain Controllers, Certificate Authorities, Active Directory Federation Services, and Exchange Servers.
We identified three trend lines:
- Before PrintNightmare publication (until June 29th)
- Publication day and three days later (June 30th – July 3rd)
- Following days (July 4th and onwards)
Before the PrintNightmare publication, only 12% of the critical assets already disabled the print spooler service therefore PrintNightmare couldn’t impact them directly.
Once the flaw was disclosed on June 30th and the CISA (Cybersecurity and Infrastructure Security Agency) encouraged administrators to disable the spooler service, especially where there was no available patch or fix, we observed a significant industry response. Organizations around the globe understood the potential risk and disabled the service causing a meaningful increase to reach 31% of critical assets with no running spooler service.
The following days were characterized by a moderate and gradual increment of companies disabling the spooler service. Yet, it reached a significant peak of 44% from the critical assets neglecting the problematic service. In this timeframe, Microsoft issued the update and later clarified its guidance.
It is key to stress that before Microsoft’s update release day (July 6th), we identified almost two-thirds (65%) of the assets as vulnerable to this severe flaw, putting the entire organization under significant security risk. As of now, more than half of the organizations are still running the spooler service.