Losing Control of Your Front Door
Analysis of Palo Alto Networks Security Device vulnerabilities
On November 10, 2021, Palo Alto Networks released advisories for eight different vulnerabilities affecting the company’s VPN firewall products. The vulnerabilities’ criticality ranges from ‘medium’ to ‘critical,’ with the most severe vulnerability, CVE-2021-3064 (CVSSv3.1 of 9.8), allowing for unauthenticated remote code execution, or RCE.
The Vulnerable Devices
Affected Palo Alto Networks products include all versions of PAN-OS 8.1 prior to 8.1.17, which was introduced in September of 2020. Shodan searches reveal that there are thousands of devices impacted by the most critical vulnerability, and nearly all such devices are vulnerable to one or more of the other high-severity vulnerabilities.
The nature of the affected products heightens the concern surrounding the impact of the vulnerabilities: in the case of a VPN connected to the public Internet, threat actors can easily transform a vulnerable device into a point of access that opens the way for nefarious actions.
With COVID-19 driving a significant shift to remote work and work-from-home initiatives, the use of remote connectivity has grown, making it a major focus for cyberhackers and other threat actors. Despite the longstanding focus of attackers on critical external applications, VPN devices have been targeted more than ever over the last 12 months. The cases of Fortinet’s FortiGate and Pulse Connect Secure serve as symptoms of a growing security problem, and the Palo Alto Networks GlobalProtect portal could prove to be yet another symptom.
Means of Exploiting the Vulnerable Devices
Currently, we know that the RCE vulnerability can be exploited from the GlobalProtect portal. Successful exploitation may lead to remote code execution, and thus, allow an attacker to obtain full control over one or more targeted devices. For now, additional details regarding ways to exploit vulnerable devices are being withheld from public consumption in order to minimize misuse.
How to Identify All of Your Vulnerable devices
Using the Forescout Device Cloud, Forescout researchers have evaluated the reported vulnerabilities and profiled the vulnerable Palo Alto Networks assets/devices. In addition, based on our research results, Forescout has released a Security Policy Template (SPT) to detect vulnerable PAN-OS instances and the severity of vulnerability associated with each device (identifying the specific CVEs affecting each device).
By leveraging this timely data and SPT created by Forescout, your organization can better protect against malicious actors seeking to exploit your Palo Alto Networks devices.
Further Detection & Mitigation Steps to Take
To solve possible breaches targeted on the above-mentioned vulnerabilities, you should install the latest version update for all of your Palo Alto Networks devices’ respective versions, making sure to first review Palo Alto Networks Best Practices.
In addition, as initial workaround and mitigation technique, Palo Alto Networks advise organizations to enable specific detection signatures to block attacks against each CVE (relevant for CVE-2021-3056/3058/3063/3064).
For CVE-2021-3059, Palo Alto advise updating dynamic content from a local file to prevent exposure to this vulnerability – until the upgrade is in place.
For CVE-2021-3060, Palo Alto advise changing the master key for the firewall to prevent exploitation of this vulnerability.
In general, to assist with mitigation of such vulnerabilities, Forescout provides three essential governing capabilities:
- Remediate
- Patch endpoints through integrations
- Fix compliance issues
- Segment
- Propose segmentation in case of vulnerabilities that cannot be remediated
- Control
- Block endpoints in case they introduce major risks that cannot get remediated or segmented (I.e., endpoints with threats)
Performing all three will optimize your ongoing security in the face of such new threats.
Demographics Data for the PAN Device Vulnerabilities
Palo Alto Networks’ VPN spread analysis
Data Source: Forescout Device Cloud
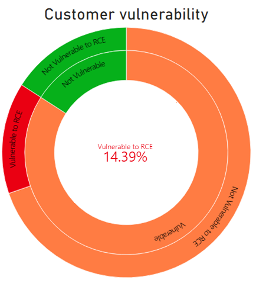
84% of the organizations we analyzed have at least one vulnerable instance, with 14% of them completely vulnerable to a severe Internet-accessible RCE (i.e., CVE-2021-3064). Only 16% are safe in the face of these recent vulnerabilities.
This analysis illustrates the struggle to both update such crucial devices and rapidly protect your network. A large number of devices remain unpatched or outdated. For example, v8.1.17, the version that solves the RCE issue, has been live for over a year. Yet, many organizations (14%) still have not performed the update.
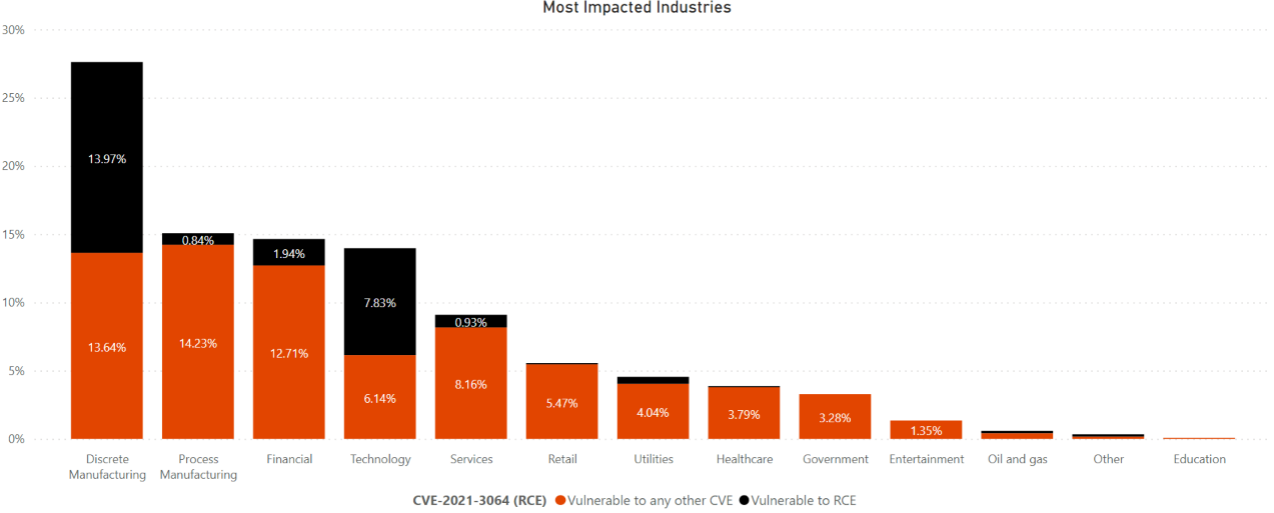
The top five industries impacted by these vulnerabilities include Discrete Manufacturing (~27.6%), Process Manufacturing (15.0%), Financial (14.6%), Technology (14.0%), and Services (9.1%). It is likely that malicious actors will soon target organizations within these industries, especially those with dense clusters of RCE-vulnerable devices (see the following chart).
Data Source: Forescout Device Cloud
It is particularly noteworthy that the Government industry has no devices that are vulnerable to the RCE. This stands in sharp contrast to our previous analyses, wherein Government frequently acted late to perform patches and mitigations deployment. This observation comes on the heels of CISA issuing a Binding Operational Directive with the purpose of significantly reducing the risk of known exploited vulnerabilities. CISA published a continuously-updating public catalog of meaningful vulnerabilities.
Version Analysis
Data Source: Forescout Device Cloud
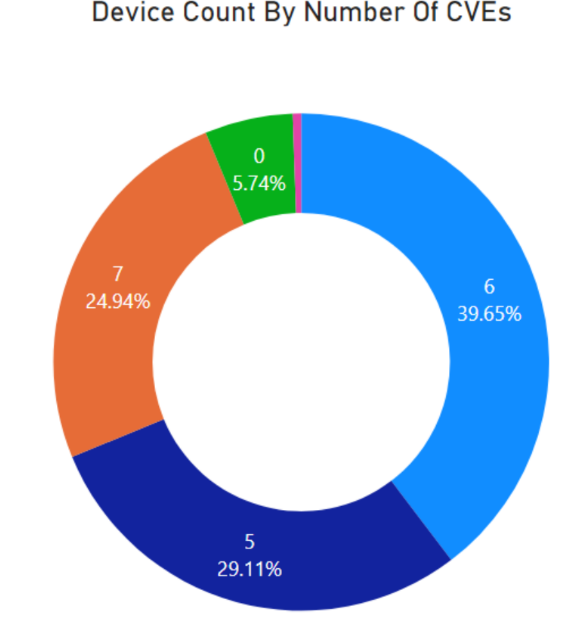
Our analysis shows that most devices (69%) are somewhat outdated, meaning they have 5-6 vulnerabilities, and a large portion (~25%) are extremely outdated and vulnerable to all* 7 vulnerabilities. Only 6% of devices are updated and have just one or zero vulnerabilities (having the most recent versions). (See data in chart to the right)
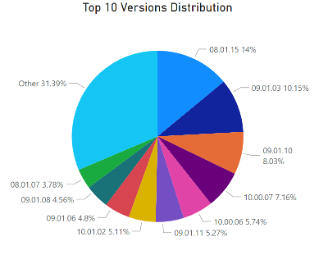
The distribution of vulnerabilities among the top 10 versions demonstrates that approximately 25% of devices analyzed are vulnerable to CVE-2021-3064, with the top version being vulnerable as well.
Data Source: Forescout Device Cloud
*The “All vulnerabilities” designation applies to the value of 7, because one of the 8 vulnerabilities affects only the VM series, which is rarely found in our data.
Conclusion
Palo Alto Networks’ latest device vulnerabilities underscore the prolonged struggle between stability and security. However, in this case, the scales tip dramatically toward security. The impact of a breached VPN has proven to be a problem which no organization wants to face. As such, any organization would be well-advised to deal with the consequences of rushing a version update rather than having to deal with an exploited VPN device.
While there are currently no known exploitations in the wild, threat actors will assuredly learn how to successfully exploit these vulnerabilities soon. A remote code execution on a default public-facing device is rare, increasing the likelihood that it will be traded and used in the short-term future.
We advise Forescout customers to install the SPT to identify vulnerable instances and patch them immediately. For all other organizations, contact Forescout today to learn how we can help you to detect and mitigate these vulnerabilities and others like them.