Forescout 8.2: The Power to Act – Fast
By 2023, the overall number of “connected” devices worldwide will increase to over 35.2 billion according to IDC.1 Staggering though this number is, more worrying is what organizations know, or don’t know, about those devices. According to a 2019 Ponemon study, breaches resulting from “unsecured IoT devices or applications increased from 15 percent to 26 percent in just three years.” 2 What’s more, the same study warns this percentage could be low, because “organizations are not confident that they are aware of all the unsecured IoT devices and applications in their workplaces and in third parties.”
Rethinking device visibility across a network of networks
Lack of visibility into a growing number of unsecured devices is a major driver for digital transformation at the network. The disappearance of monolithic, flat networks with hard perimeters adds to the urgency for change. IoT and unmanaged devices are connecting through a network of networks. Increasing numbers of employees either work from home or from a shared workspace. Those employees connect to the corporate network infrequently. On top of that, applications are leaving the corporate network as companies transition to SaaS solutions, or move their own applications to public and private clouds. Plus, many IoT devices connect through other networks and never connect directly to the corporate network.
No matter where or how devices connect, a single weak spot on any interconnected network can leave an organization vulnerable. Fundamentally, we need to think about control in terms of device access, not just network access. The one thing that’s essential for protecting devices and networks is complete device visibility. A single source of truth for all connected devices, including what those devices should be able to do. But it’s only the beginning. Once we have complete visibility and have identified risk, we need to take action – fast.
Forescout 8.2 breaks down barriers to action
Breaking down barriers to action by streamlining security operations—it’s the driving principle behind Forescout 8.2. The latest iteration of the Forescout platform can help security and IT leaders use the complete visibility it provides to collaborate more efficiently across teams, integrate more quickly across technologies, and act faster and with more confidence to mitigate risk.
With Forescout 8.2, you can:
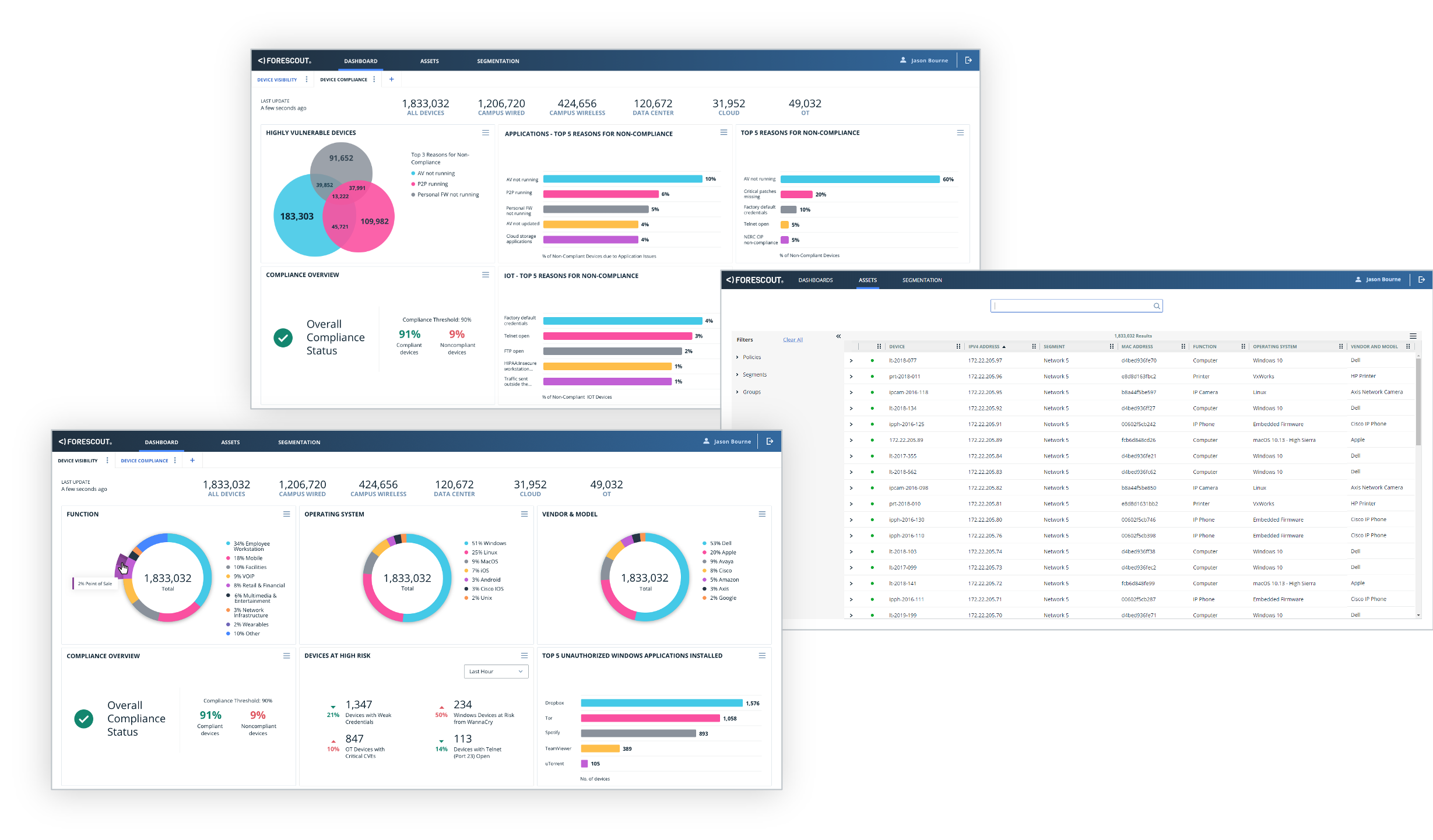
- Pinpoint and prioritize. The new user interface helps all stakeholders get more from the device context and actionable insight in eyeSight. Out-of-the-box dashboards for device visibility and compliance alert teams quickly to areas of highest risk while helping teams meet user-defined compliance goals. Simple customization and sharing options make it easier to personalize views, and to collaborate more effectively across IT functions for faster decision-making and response.
- Get proactive. The new web-based asset view brings all your connected devices together so you can search, sort and filter your asset inventory across campus, data center, cloud and operational technology. Find at-risk assets for faster MTTR.
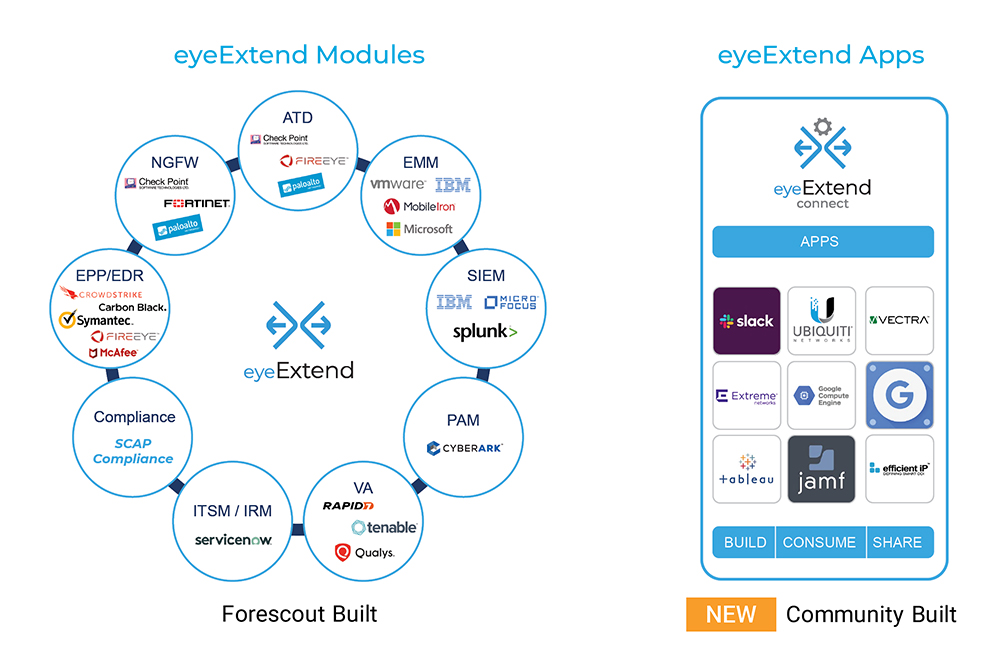
- Integrate faster. Customers and partners can quickly build, consume and share apps to connect with the Forescout platform thanks to Forescout eyeExtend Connect, a new community-based app ecosystem. It lets you easily share device context with other tools, automate security workflows and take action to accelerate system-wide response to reduce mean time to resolution.
- Deploy the Forescout virtual appliance in public clouds. Cloud-first organizations can now deploy the Forescout virtual appliance in their AWS or Azure public clouds—no on-premises hardware required. This deployment option can also be combined with Forescout on-premises virtual or physical appliances, where customers want to take a hybrid approach.
As you’d expect, there are many other highlights in the Forescout 8.2 release. Forescout eyeSegment, for example, enables enterprise-wide segmentation across multiple network domains and diverse enforcement points. And SilentDefense™ is now integrated into the Forescout platform to address a variety of security and risk management use cases specific to operational technology and converged environments.
To learn more about the innovations packed into Forescout 8.2, read our What’s New datasheet, visit our Forescout 8.2 webpage and join us for a webinar to see Forescout 8.2 in action.
And consider this: No matter where digital transformation is taking your organization, Forescout can help you keep your devices and interconnected networks secure on that journey. It all starts with visibility, and the power to act – fast.
1Worldwide IoT Forecast, 2019-2023 IDC.
2Third Party IoT Risk: Companies Don’t Know What They Don’t Know, Ponemon Institute