In a new threat briefing, Forescout Research – Vedere Labs details an exploitation campaign targeting organizations running Fortinet’s FortiClient EMS which is vulnerable to CVE-2023-48788. We are designating this campaign Connect:fun because of the use of ScreenConnect and Powerfun as post-exploitation tools – our first-ever named campaign.
Here are details of an incident targeting a media company using CVE-2023-48788 with evidence pointing to a possible threat actor active since at least 2022 targeting Fortinet appliances and using Vietnamese and German languages in their infrastructure. We are closely tracking this infrastructure and will report on this actor again in the future. Access our full report to read more details of the observed incident, including log collection data and threat hunting opportunities.
On March 12, 2024 Fortinet published an advisory about CVE-2023-48788, a SQL injection vulnerability in the FortiClient EMS security management solution. On March 21, researchers released a proof of concept (PoC) exploit for the vulnerability and since then there have been reports of exploits in the wild leading CISA to add the CVE to its list of Known Exploited Vulnerabilities (KEV) on March 25.
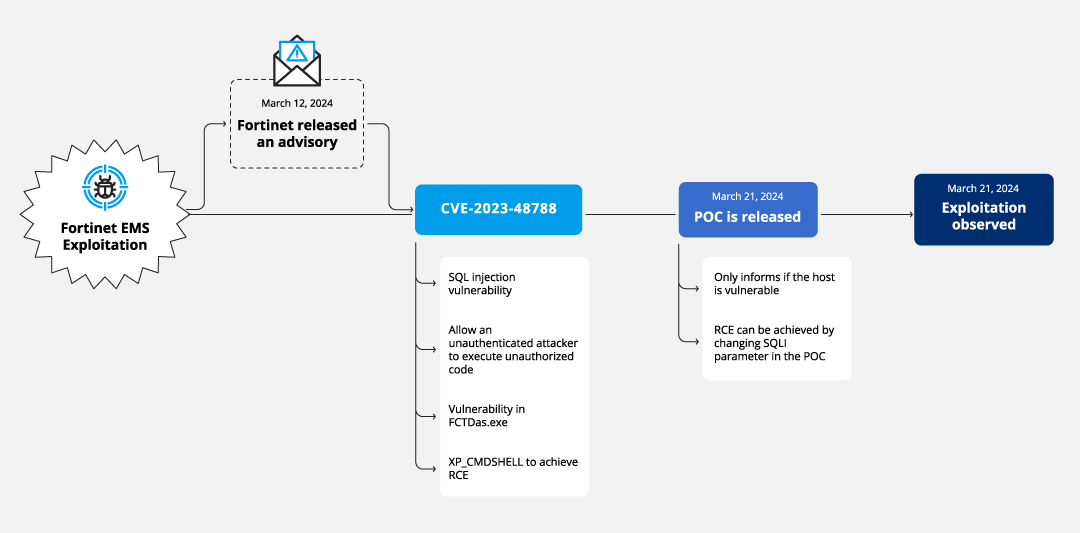
Exploit details of CVE-2023-48788
Since the PoC for CVE-2023-48788 was made available on March 21, we have observed exploitation attempts similar to the PoC. Here we discuss one specific incident that targeted a media company whose FortiClient EMS was vulnerable and exposed to the internet.
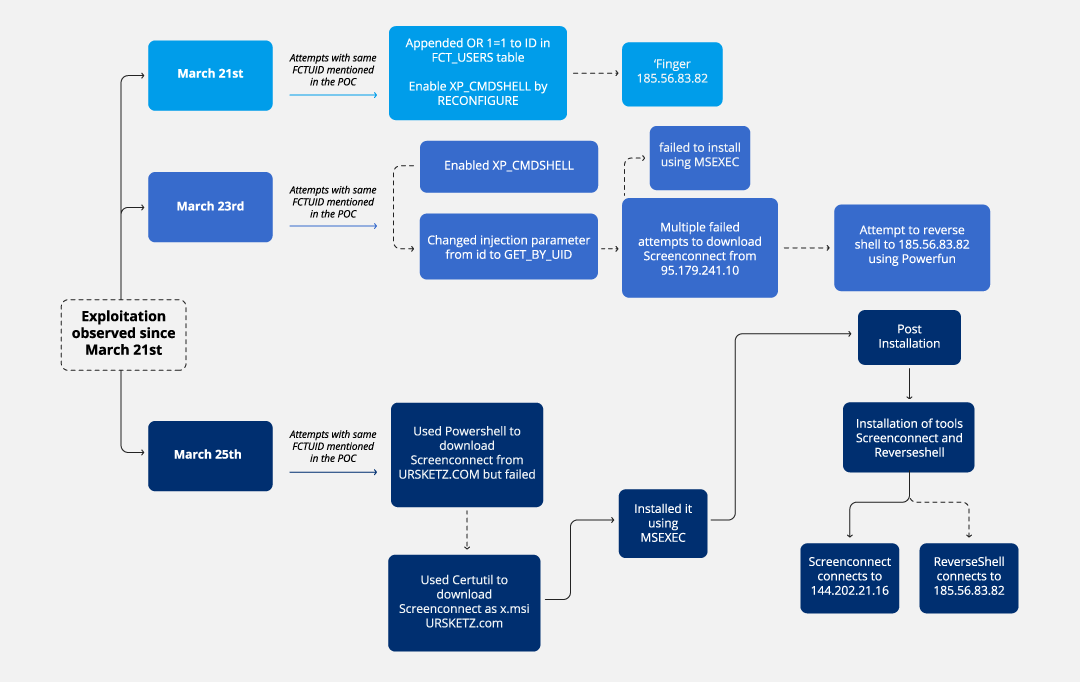
On March 21, server logs show that the threat actor tried to achieve command execution via a sequence of commands to enable advanced configuration options and the xp_cmdshell stored procedure in SQL Server. Right after the changes, the threat actor used the LOLBAS finger.exe to download a malicious payload from 185[.]56[.]83[.]82 but was unsuccessful because of using the incorrect syntax.
Two days later on March 23, the same actor executed “FINGER [email protected]” along with “WAITFOR DELAY ’00:00:10′ –” to check if the command was executed and to see if the vulnerability still existed. Though the command was not successful, the DELAY might have hinted to them that the host was still vulnerable.
After the actor confirmed the host was still vulnerable, they executed several SQL injections with obfuscated commands to download the ScreenConnect remote management tool and a malicious script based on the open-source Powerfun which includes functionality for bind and reverse shells, as well as execution of arbitrary commands from (Command and Control).
After a couple of days, we saw multiple SQL statements trying to download ScreenConnect using a domain ursketz[.]com. The file names earlier downloads seen from IP address 95[.]179[.]241[.]10.
The actor used certutil.exe to download ScreenConnect and install it using msiexec.exe. The attempt to download and install was successful. This is also confirmed by the firewall logs, where we observed traffic to the domain used to download ScreenConnect hosted at 141[.]136[.]43[.]188.
Connections from ScreenConnect were destined to 144[.]202[.]21[.]16 but we were not able to retrieve the ScreenConnect logs to identify further actions.
Analysis: Campaign and threat actor details
This incident was not isolated. We observed scanning activity from the same IP address 185[.]56[.]83[.]82 for FortiClient EMS in other customer networks beginning March 21 which continued on March 22nd, March 25th and March 28th. The timeframe is consistent with exploitation attempts shown above — and was observed in customers who do not use FortiClient EMS in their environment but use other VPN appliances. However, we do not see indiscriminate automated exploitation attempts on honeypots as we have seen in the past with other vulnerabilities on edge devices. The activity clearly has a manual component evidenced by all the failed attempts to download and install tools, as well as the relatively long time taken between attempts.
This is evidence the activity is part of a specific campaign rather than an exploit included in automated cybercriminal botnets. From our observations, it appears that the actors behind this campaign are not mass scanning but choosing target environments that have VPN appliances.
Other cybersecurity companies [1] [2] have also seen similar incidents with the exploitation of CVE-2023-48788 to download RMM software, including ScreenConnect and Atera. All the reports we have seen are similar, including IP addresses and infrastructure that intersect with our observations and bear hallmarks of manual exploitation.
The IPs and domains involved in the incident we described above were also involved in previous cases:
- 185[.]56[.]83[.]82 tried to login to Fortinet SSLVPN appliances on March 14, a couple of days after the Fortinet advisory was released and before the public PoC for CVE-2023-48788. We also observed the same activity on March 25 and 27. This IP address was also seen in 2022 trying to login to several Fortinet SSLVPN appliances and using similar techniques to download and execute malicious payloads.
- 144[.]202[.]21[.]16 is part of AS20473 and had ports 3389 and 5985 available with hostname “vultr-guest” at the time of the incident. This is the default hostname for endpoints hosted by Vultr, which was known to host threat actor infrastructure for actors exploiting FortiGate appliance vulnerability CVE-2018-13379 in 2022. Another IP address mentioned in a similar FortiClient EMS incident observed by another company was 45[.]77[.]160[.]195, which is also hosted by the same provider.
- 95[.]179[.]241[.]10 has an associated domain name of ls[.]vfxtraining[.]shop and is also hosted on AS20473 by Vultr (with the same hostname “vultr-guest”). The host had open ports 22/SSH, 2053/HTTP, 2083/HTTP, 2087/HTTP, 2096/HTTP, 8443/HTTP and 8888/HTTP on which we could see the certificate common name mci11[.]raow[.]fun. Pivoting off this name, we could obtain additional IP addresses spread over Germany, United Arab Emirates and United Kingdom. The site also has one open directory with files such as adduser, delete, kill.php, killusers.sh, online.php, syncdb.php and token.php.
- ursketz[.]com was contacted by a suspicious PowerShell script named jpeg.lnk on April 12, 2021. That script tries to download files from a GitHub repository, now offline, that had a folder “Project Nhap mon an toan thong tin” (English translation: “Project Introductory Information Security”) and several suspicious DLL, EXE and SH files.
- ursketz[.]com resolved to 2a02:4780:a:952:0:1e10:e79b:1 (IPv6) and 141[.]136[.]43[.]188 (IPv4) at least from 2022. A snapshot of the website from July 21, 2022 shows the title “UrSketz – Digital Assets Investment Company” with content in German. The address on the page is an office building in Germany.
The evidence points to a possible, active threat actor since at least 2022 targeting Fortinet appliances using Vietnamese and German languages in their infrastructure. Initially perceived as a security team or research team in Vietnam based on the Github repository, they are actively exploiting and installing tools post-exploitation on real targets instead of only researching.
Mitigation recommendations, TTPs and IoCs
To mitigate against exploitation of CVE-2023-48788, follow these steps:
- Apply the patch provided by Fortinet.
- Ensure that the traffic reaching FortiClient EMS is constantly monitored for signs of exploitation by using an intrusion detection systems (IDS).
- Consider using a web application firewall (WAF) to block potentially malicious requests.
- Use the IoCs and TTPs shared below for threat detection and hunting in your network.
The following IOCs come from the incident we described and others shared by the community.
| Type | Indicators |
|---|---|
| IP addresses | Seen in our incident:
141[.]136[.]43[.]188 (IPv4) / 2a02:4780:a:952:0:1e10:e79b:1 (IPv6) 144[.]202[.]21[.]16 185[.]56[.]83[.]82 95[.]179[.]241[.]10
Seen in other incidents: 45[.]77[.]160[.]195 216[.]245[.]184[.]86 |
| URLs / Domains | Seen in our incident:
mci11[.]raow[.]fun
Seen in other incidents: hxxp[:]//45.227.255[.]213:20201 hxxp[:]//68[.]178.202.116 jxqmwbgxygkyftpxykdk8cfkq1hy371pz.oast[.]fun |
| Hostnames | “VULTR-GUEST” |
| ATT&CK TTP | Procedure examples | Detection |
|---|---|---|
| T1190 – Exploit Public-Facing Application | SQL injection like statements in application specific folders | Network |
| T1219 – Remote Access Software | Common RMM IP/domain connections | Network |
| T1059.003 – Windows Command Shell | Certutil.exe running on command shell | Endpoint |
| T1059.001 – PowerShell | Suspicious powershell.exe commands | Endpoint |
| T1027 – Command Obfuscation | Use of CHAR() on SQL injection payloads | Endpoint |
| T1105 – Ingress tool transfer | Certutil.exe downloading binaries | Endpoint |
| T1133 – External remote services | Connections to/from VPN networks
Connections to new sites from appliance servers |
Network |
| T1218.007 – Msiexec | Msiexec.exe executing malicious payloads | Endpoint |