Quantum computing isn’t coming. It’s already here, and its an arms race for supremacy. The world’s financial leaders just put a date on when organizations must be ready to protect itself.
The G7 Cyber Expert Group (CEP) recently released a coordinated roadmap for transitioning to post-quantum cryptography (PQC) in the financial sector, establishing 2030-2035 as the critical window for migration. According to the roadmap, 2026 is the beginning of defining your PQC strategy. But you could be flying blind. Information you don’t have may be hindering your ability to strategize.
While the guidance targets financial institutions, the implications extend far beyond banking. Every organization managing sensitive data – from government agencies to healthcare providers to critical infrastructure operators – faces the same threat in the quantum computing supremacy timeline.
The message is clear: the era of ‘harvest now, decrypt later’ attacks is already underway, and the window to protect against quantum computing threats is closing faster than many realize.
What the G7 Roadmap Reveals
The G7’s statement doesn’t set binding regulations, but it does something equally powerful: it establishes a coordinated framework that will likely influence policy worldwide.
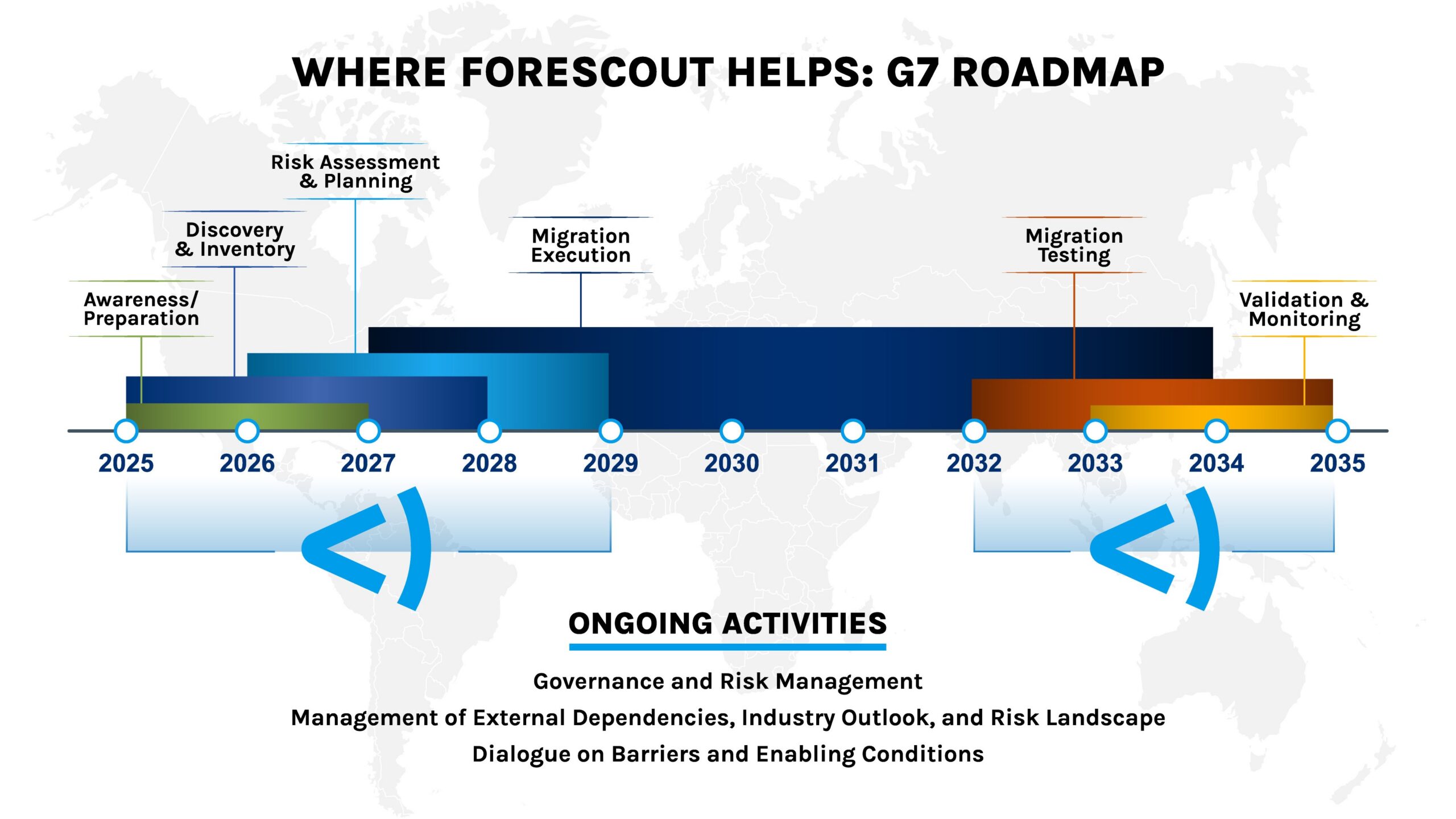
The roadmap outlines six critical phases:
- Awareness & Preparation (2026-2027): Executive-level risk awareness and initial PQC resilience strategy
- Discovery & Inventory (2027-2028): Comprehensive inventory of cryptographic assets and dependencies
- Risk Assessment & Planning (2028-2029): Tailored migration plans for critical and non-critical functions
- Migration Execution (2030-2032): Progressive deployment of quantum-resistant solutions, prioritizing critical systems
- Migration Testing (2032-2034): Validation of migrated functions and ecosystem testing
- Validation & Monitoring (2035+): Continuous validation and adaptive frameworks
“[O]rganizations may benefit from beginning migration as soon as relevant products and standards become available and are validated for their specific use cases,” explains the authors in the CEP statement. “Organizations may also benefit from incorporating a goal of cryptographic agility in their transition plans to adapt new cryptographic solutions for emerging threats and vulnerabilities.”
See the full G7 statement from January 2026.
Crucially, the G7 emphasizes that these phases aren’t strictly linear. Organizations must pursue multiple activities in parallel while maintaining flexibility to adapt as the threat landscape evolves.
The Reality Check: Where Organizations Stand Today
Forescout Research—Vedere Labs recently shared analysis on global PQC adoption, and the findings are sobering:
- Only 8.5% of SSH servers worldwide support post-quantum encryption.
- Less than 20% of global communications use TLSv1.3, the only complete TLS version supporting PQC.
- TLSv1.2 adoption – which doesn’t support PQC – actually increased from 43% to 46% between April and August 2025.
- Unsupported adoptions of PQC have already been debunked.
- Among devices running OpenSSH, 42% of IT assets support PQC, but only 20% of IoT, 11% of OT and network equipment, and just 2% of IoMT devices do.
The data reveals a troubling pattern: early adopters are migrating quickly, but adoption rates are plateauing. Industries heavily reliant on unmanaged devices – manufacturing, oil and gas, mining – show the lowest PQC readiness. Network infrastructure devices like routers, firewalls, and VPN appliances remain particularly vulnerable, and are prime targets for ‘harvest now, decrypt later’ attacks.
Forescout’s Quantum-Safe Security Assurance
Recognizing that you can’t secure what you can’t see, Forescout developed and patented breakthrough technology to detect and inventory quantum safe and non-quantum-safe encryption usage in real time, without agents. It’s the first solution of its kind. This innovation analyzes cryptographic ciphers across every connected asset, scoring them against post-quantum safety standards based on their identity, behaviour and overall risk profile
Unlike static assessments that only verify if devices support quantum-safe encryption, Forescout’s technology monitors actual behavior. It detects when devices communicate using unsafe ciphers, even when they’re capable of better or not. This distinction matters because devices can be tricked into downgrading to vulnerable encryption, creating exposure even in supposedly secure environments
The Forescout 4D Platform™ delivers a comprehensive quantum-safe strategy aligned with the G7 roadmap phases:
Detect (Awareness & Discovery Phases): Forescout’s patented technology identifies PQC-safe and non-safe assets in real time, providing the comprehensive cryptographic inventory the G7 roadmap demands.
Assess (Risk Assessment & Planning Phases): With Forescout eyeSegment, organizations can isolate critical systems and secure communication pathways through network segmentation—a crucial step before migration begins.
Control (Validation & Monitoring Phase): Forescout protects at-risk devices by limiting their traffic, providing ongoing assurance that quantum-vulnerable communications don’t compromise security.
Govern (Migration Execution & Testing Phases): Backed by threat intelligence from Forescout Research – Vedere Labs, Forescout detects rogue assets or misconfigurations to swiftly target policy enforcement during the migration process.
What Organizations Should Do Now
The G7 roadmap provides a blueprint, but action requires understanding your specific exposure. Here’s how to start:
- Classify Data by Sensitivity and Longevity
Not all data requires the same urgency. Information that loses value quickly poses less risk than sensitive data with long-term value—diplomatic communications, research, intellectual property, personally identifiable information, or financial records that must remain confidential for decades. - Build a Comprehensive Cryptographic Inventory
You cannot migrate what you cannot see. Deploy solutions like Forescout that provide real-time visibility into which devices use quantum-vulnerable encryption. This inventory must extend beyond traditional IT to include IoT, OT, and IoMT assets. - Correlate Inventory with Contextual Risk
A TLS 1.2 connection using RSA-2048 might seem dangerous in isolation, but context matters. Is it protecting ephemeral traffic in a hardened enclave, or is it securing long-term storage of merger documents? Risk scoring must account for exposure, data sensitivity, and threat landscape. - Prioritize Based on the G7 Timeline
Critical systems handling sensitive, long-lived data should target the 2030-2032 migration window. Less critical systems can follow extended timelines, but all should be planned for completion by 2035. - Design for Cryptographic Agility
“Quantum-safe” today doesn’t mean “quantum-proof” forever. The algorithms we implement now will evolve as our understanding of quantum threats deepens. Build key rotation and algorithm flexibility into your cryptographic frameworks from day one.
The Post-Quantum Cryptographic Path Forward
The G7’s coordinated roadmap represents a watershed moment in cybersecurity. It’s that rare opportunity to get ahead of a generational threat before urgency overtakes strategy.
Financial institutions will lead the migration, but every sector must follow.
For organizations beginning this journey, the challenge is immense but not insurmountable. The Forescout 4D Platform™ provides the visibility, control, and quantum agility required to navigate crucial phases of the G7 roadmap — from initial discovery through continuous validation.
The quantum computing era will redefine digital trust. Organizations that act now will secure their future. Those that wait risk becoming casualties of a threat they saw coming but failed to prepare for …
The countdown to Q-Day has begun. The question isn’t whether to migrate to post-quantum cryptography. It’s whether you’ll take control before the threat arrives.
Talk to us about our Quantum-Safe Security Assurance and patented PQC detection technology.