Solutions
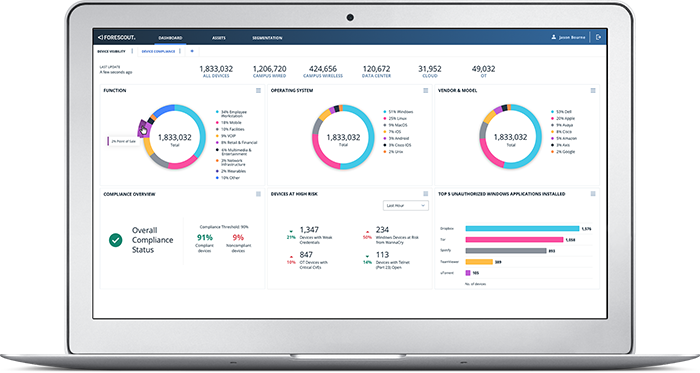
The attack surface is growing. So is Forescout.
Our leading network security solutions for cyber asset management, network access control, segmentation management, and OT/ICS and IoMT security are now part of a broader portfolio that encompasses risk and exposure management and threat detection and response – all on a single, scalable, vendor-agnostic platform.