Network segmentation is a security best practice, but is adoption lagging in healthcare?
Healthcare delivery organizations (HDOs) are repeatedly cited as lagging when it comes to cybersecurity practices—and consequently, healthcare is also often the most targeted industry. A recent study found that healthcare organizations and hospitals report one fourth of all U.S. cyberattacks, making healthcare the number one industry impacted by data breaches. And, there have been no indications that attackers are going to back off anytime soon, with ransomware attacks on healthcare organizations alone anticipated to quadruple by 2020.
So, why is it that healthcare organizations are hit so hard and so frequently and what can be done to alter that trend? That’s one of many questions our researchers asked when they performed an in-depth analysis of the Forescout Device Cloud, a repository of host and network information for more than 10 million devices and one of the largest crowdsourced device repositories. For this study, researchers limited Device Cloud analysis to 75 healthcare deployments with over 10,000 virtual local area networks (VLANs) and 1.5 million devices. Since the primary focus of the report is the status of medical devices, many of the results are based on analysis of more than 1,500 medical VLANs with 430,000 devices. Access the full report: Putting Healthcare Security Under The Microscope.
To be fair to the healthcare industry, it’s important to understand that HDOs have some very specific requirements that sometimes create unique security challenges. Within the confidentiality, integrity and availability (CIA) triad, healthcare providers prioritize availability as a means to patient safety, which sometimes requires that long-lived legacy devices continue to operate in the HDO environment. Those devices may pose a security risk, but oftentimes those devices are critical to patient care.
Ultimately, we found a number of contributing factors to the HDO security problem. As discussed in our blog titled, Remember the Windows XP problem? End-of-support for Windows 7 is next, and it might be even worse, not only are there devices on healthcare networks still running an unsupported operating system (OS), but more than 70% of devices are running a Windows OS that will no longer receive extended support after January 14, 2020 (e.g., Windows 7) unless extended support is purchased—and even those extensions will eventually end.

If not addressed, the security problem will only become exacerbated by the volume of devices running legacy Windows in healthcare environments.
Additionally, in support of HDO practitioner common knowledge, we found further evidence that medical networks are indeed complicated. Roughly 53% of the devices were categorized as traditional computing (IT) devices, 39% were categorized as IoT devices, and 8% were considered operational technology (OT) devices.
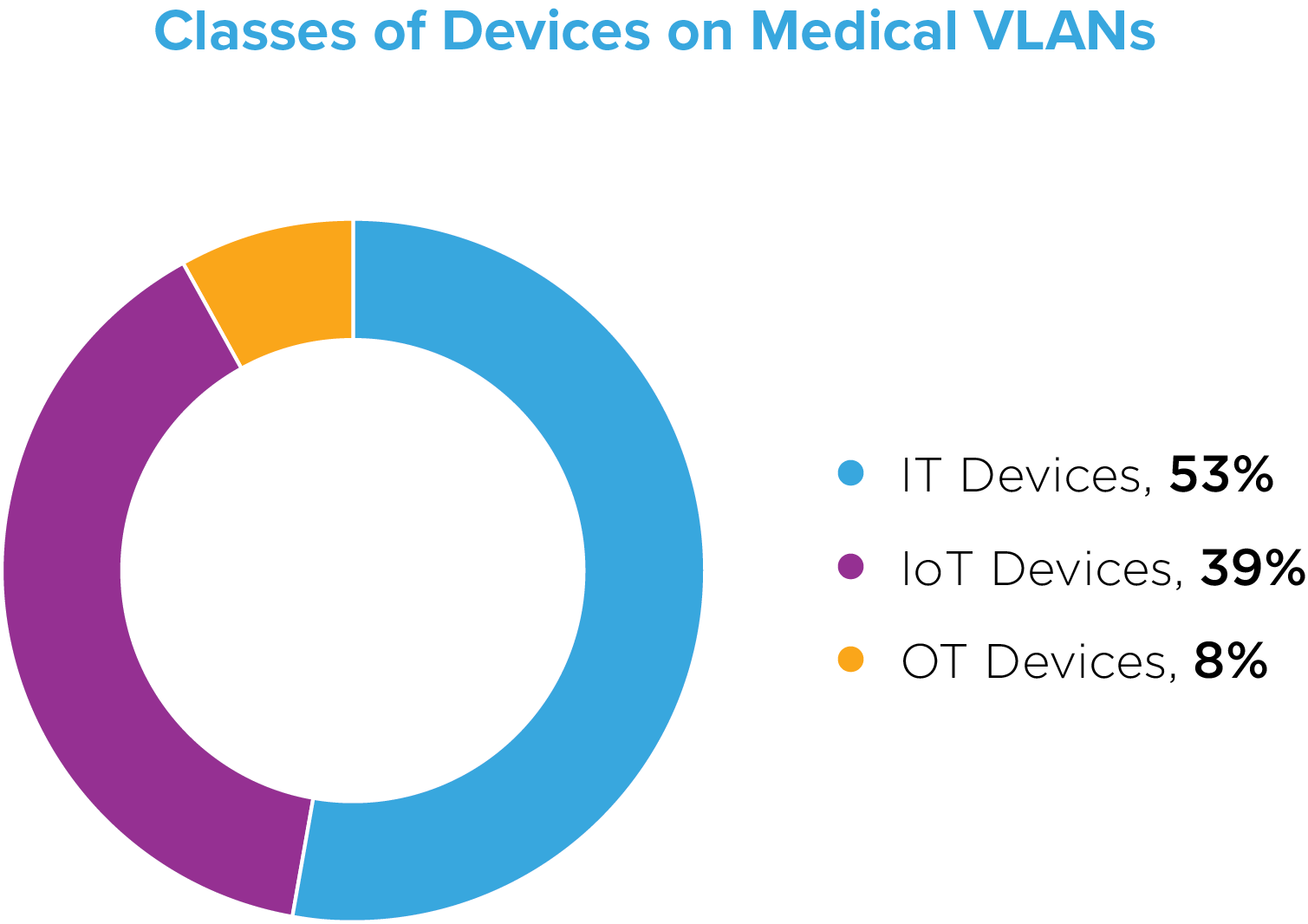
These findings not only highlight the convergence of IT, OT, IoT and Internet of Medical Things (IoMT), but also the siloed nature of security within HDOs. Various teams focus on their specific area of responsibility. Clinical engineers and medical technicians, for example, may play a hybrid role of both system owner and custodian, and be responsible for both using and securing the devices, as well as managing remote access vendor personnel. Separately, facilities and operations teams may in turn concentrate on securing the building automation systems and operational technologies encompassing such clinical and biomedical networks.
First, fixing the legacy Windows problem is a challenge. Updating legacy operating systems may seem like the most practical approach to improving security, but the reality is that such an update can be costly and takes time to implement successfully. Right now, many HDOs may already be in the process of such updates, but the problem is further complicated by the fact that some of the devices running a legacy OS are shared-use devices—things like MRI and CT scanners, which typically have a long-life expectancy. These big, shared-use devices are expensive, and in comparison to smaller single-use devices, there are often fewer of them within a given healthcare environment. As such, and because of the healthcare focus on patient safety, many HDOs simply cannot afford to take a device offline for an update. And, even if an HDO has the luxury of taking a machine offline temporarily for an update, there’s no guarantee that an upgrade for security reasons will leave functionality of critical applications intact. It’s not uncommon for updates to ‘break’ applications. When it comes to healthcare, patient safety and system availability remain the top priority, so HDOs must evaluate the risk accordingly.
Second, correcting the commonly found security stovepipes would require intensive culture, process, responsibility and accountability changes. While these types of changes might be less costly than other alternatives, they are often time-intensive and overcoming resistance to the change can be difficult to manage.
Moreover, as we waded through these findings and others, we realized that the healthcare organizations, hospitals, clinics and other HDOs could greatly improve their security posture by taking a context-aware approach and employing advanced network segmentation.
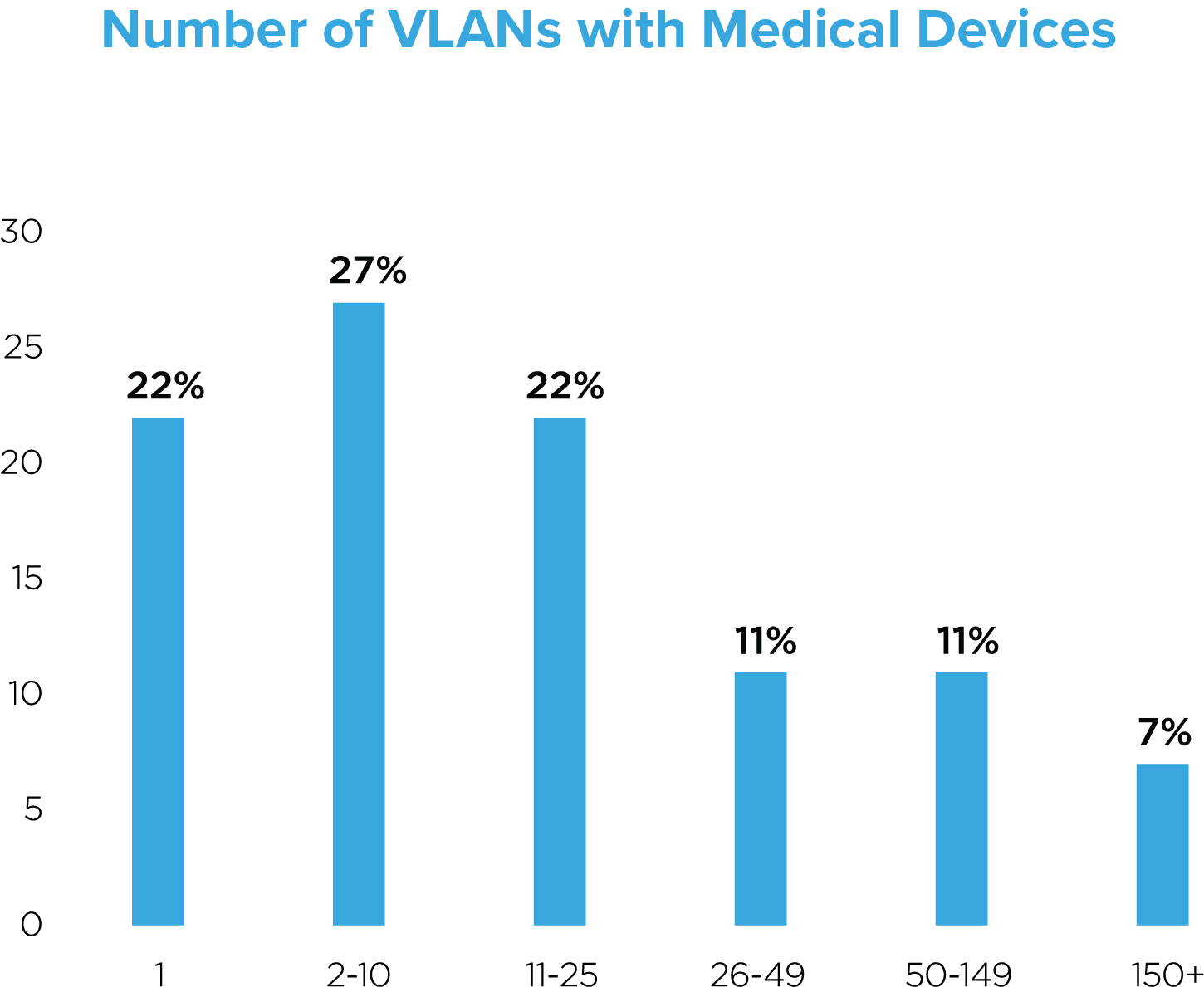
To solidify that theory, we queried the number of VLANs across our sample. For the purposes of our research, VLANs are commonly used as segmentation zones; the more zones you have, the better segmented your network is. As depicted below, we found that only 22% of deployments in our sample had healthcare devices on 11-25 zones, 11% had devices on 26-49 zones, another 11% had devices on 50-149 zones and only 7% had devices on 150 or more zones, leaving 49% of deployments with devices on 10 zones or less.
To put that in context, consider the device-to-zone-ratio akin to a student-to-teacher-ratio in schools. The more connected devices (i.e., students) there are, the more zones (i.e., teachers) you ought to have. Our findings also revealed a broad array of IT, OT and IoT devices, and within each, there’s a host of different devices, many of which have a unique function and widely varying security. Some devices might be patched, properly segmented, and just about as secure as they can be—while others might never have been patched or are connected to public Wi-Fi.
It’s hard to assign an appropriate recommendation as to how many segmentation zones an HDO should have—HDO size, complexity, resources and device count are but a few important factors to consider, but overall, the fact that 49% of the HDOs in our sample had 10 zones or less, suggests that segmentation is not being leveraged as heavily as it should be.
Why segment?
First, network segmentation is considered a best practice by many in the industry and is cited in the National Institute of Standards and Technology (NIST) SP800-125. Second, it’s important to realize that segmentation isn’t a single approach or solution that will solve every security risk. However, when used in tandem with other best practices, it can provide an organization with a more comprehensive defense strategy.
At a high level, a well-implemented segmentation approach will put like devices on the same zone . For HDOs, that might mean putting all connected medical devices on one zone, but putting shared-use devices like MRI and CT scanners on a separate zone. Alternatively, an HDO might opt to segment by the floors in the building, or choose to separate hospital-owned devices from patient and employee-owned devices. There are many ways to go about segmentation and an effective deployment may require multiple segments, depending on resources, budget and risk appetite. In particular, legacy devices running obsolete OS versions require special attention and dedicated segments.
The primary benefit of device-based segmentation is that if an attacker were to gain access to a single device on an organization’s network, their ability to move laterally and infect other devices can be significantly limited, controlled and ultimately stopped. And, because it’s important to understand how an attacker gained unauthorized access in the first place, segmentation can enable cyber defenders and investigators to more easily trace the path back to the point of entry, enabling the organization to better secure the network against future attacks.
Learn more about network segmentation and Forescout’s context-aware approach.
