The Forescout Platform
Manage risks. Contain events. Mitigate threats.
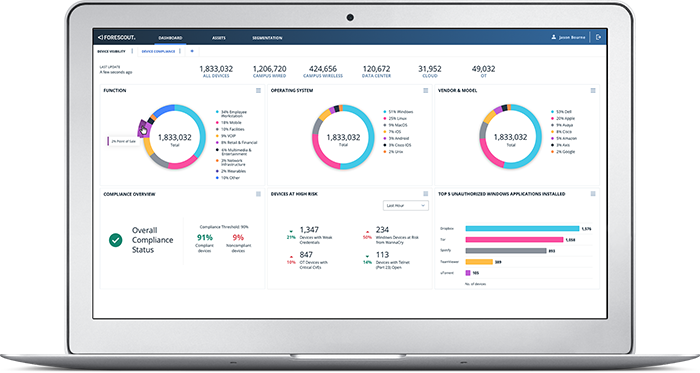
The Forescout Platform continuously identifies, protects and ensures the compliance of all managed and unmanaged cyber assets – IT, IoT, IoMT and OT – without business disruption. It delivers comprehensive capabilities for network security, risk and exposure management, and extended detection and response. With seamless context sharing and workflow orchestration via ecosystem partners, it enables you to more effectively manage cyber risk and mitigate threats.