Risk and Exposure Management
Forge Your
Cybersecurity Safe Zone
Identify, prioritize, and mitigate cybersecurity risk and exposure to help ensure compliance at every level
Schedule a demo download solution brief
Gartner® 2024 Strategic Roadmap for Managing Threat Exposure
Effectively managing threat exposure requires continuous assessment of vulnerabilities, proactive measures and strategic countermeasures. This guide offers security and risk leaders valuable insights, actionable plans, and best practices for developing strategic plans to tackle security issues.
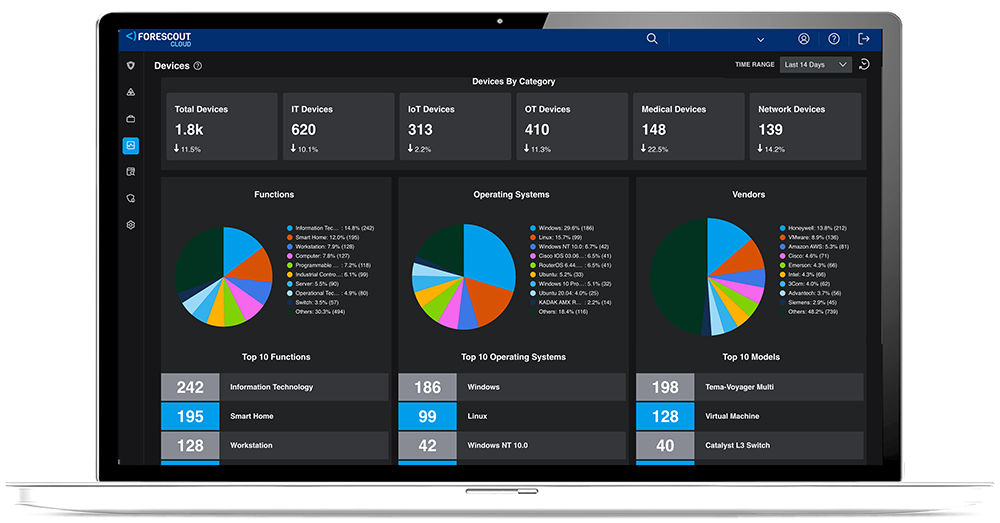
Identify Exposures
Leave No Asset Unseen
Especially the Unmanaged Ones
Continuously identify exposures across all cyber assets, managed and unmanaged, for real-time visibility of the attack surface.
- Enhance efficiency with an all-in-one solution for identifying all IT, IoT, OT and XIoT cyber asset exposures
- Optimize performance and measure progress with comparing historical data against goals
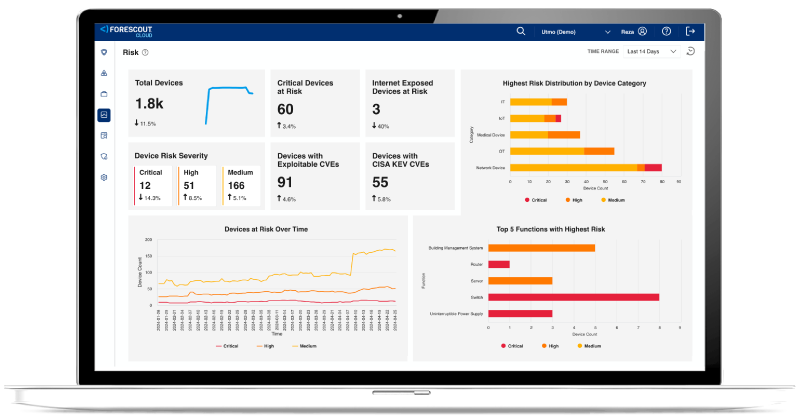
Prioritize Risks
Find the Weakest Links
Before Attackers Do
Strategically assess and prioritize asset risks to make better security and business decisions.
- Ensure business continuity and resilience by focusing on critical risks affecting key assets
- Optimize resource allocation by targeting high-priority risk exposures
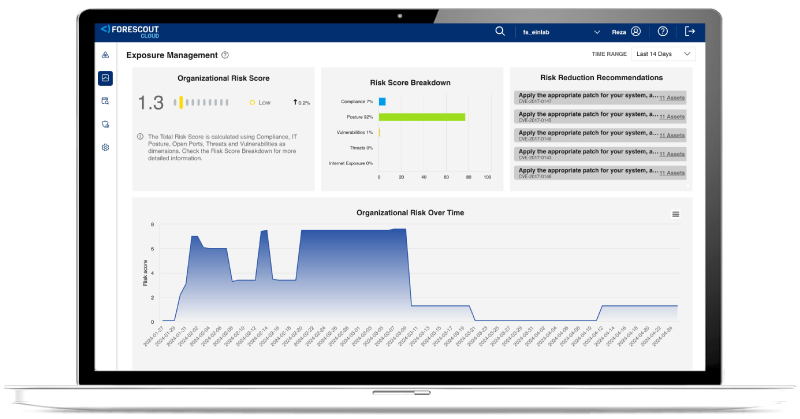
Mitigate Threats
Stay Ahead, Own Compliance,
and Avoid the Aftermath
Improve your organizational risk posture with actionable mitigation plans to ensure compliance standards are met.
- Proactively enhance security effectiveness and risk mitigation with actionable recommendations
- Boost customer trust and gain a competitive edge with proactive threat mitigation
Use Cases
Attack Surface Management
Gain full visibility, identify threats & protect your cyber assets
Continuously identify and mitigate risks across your entire cyber asset attack surface in real-time, including IT, IoT, OT, IoMT, to gain insights into your assets’ usage and its associated risks.
Third Party Risk Management
Don’t let a compromised third party put your business at risk
Proactively identify and prioritize the impact of potential exposures for every connected asset, including your third party and supply chain partners to mitigate the potential threats.
Ransomware
Readiness
Stay one step ahead & secure your business against ransomware attacks
Prevent ransomware effectively by proactively identifying and assessing potential exposures within your organization and implement targeted measures to eliminate them.
Compliance
Assurance
Manage your cyber risk effectively to stay compliant & confident
Comprehensive visibility into exposure gaps, such as misconfiguration, weak security postures and undesired network connectivity to ensure smoother audits.
Recommended Resources
2023 Threat Roundup Report
Dynamic Network Segmentation in the Age of Zero Trust
Closing the Gap: A Proactive Approach to Mitigating Cyber Risks
Schedule a Demo
Get a personalized tour of our Risk and Exposure Management offering and see how we can help you automate cybersecurity.