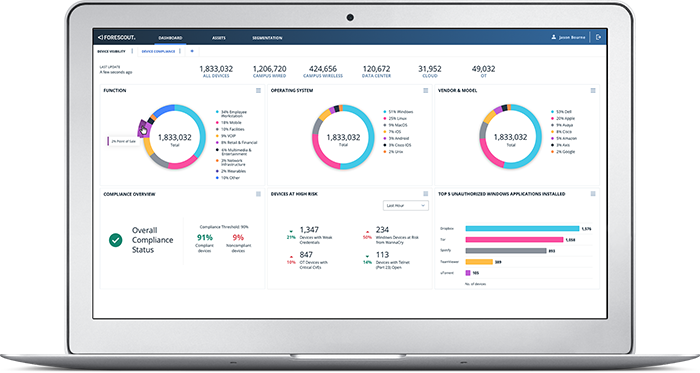
Achieve Maturity Level 3 with all Essential Eight controls
The Australian Cyber Security Centre’s (ACSC’s) Essential Eight Maturity Model is a set of mitigation strategies designed to improve cybersecurity posture by making it hard for adversaries to compromise networks. With three maturity levels, even organisations with scarce IT resources can achieve baseline compliance and protection from increasing cyber threats. And with continuous visibility, compliance assessment and automated workflows using the equipment and security tools you already have, your network can adapt to your ever-changing digital terrain.
The Essential Eight is a set of mitigation strategies, not a single solution or technology that can be bought through a single vendor. They address three areas that require not only different security tools but tight communication and coordinated actions. Either natively or by coordinating automated actions among security tools, Forescout enables you to achieve Maturity Level Three for all eight controls, with continuous visibility into granular compliance status.
LEARN MORE