Compliance Center
Manage Risk and Enforce Compliance with Forescout.
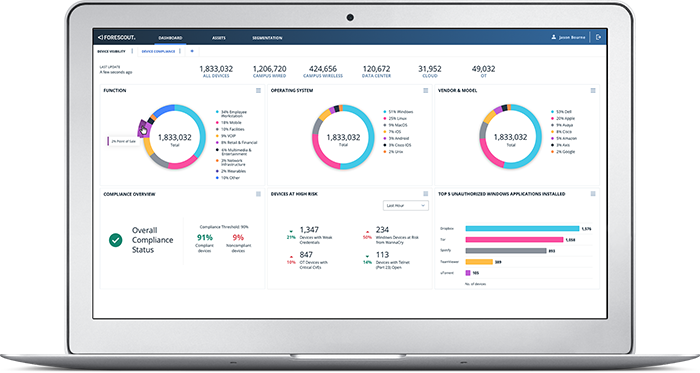
New devices constantly connect to your network – everything from managed endpoints, BYOD and other unmanaged devices, IoT, virtual machines, cloud instances and ICS/OT systems. Even rogue and unauthorized devices. Learn how to manage risk from all connecting devices and enforce device compliance to adhere to security frameworks, industry standards and regulations.