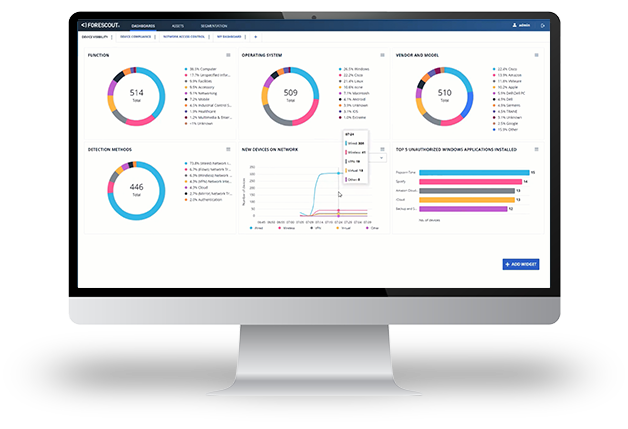
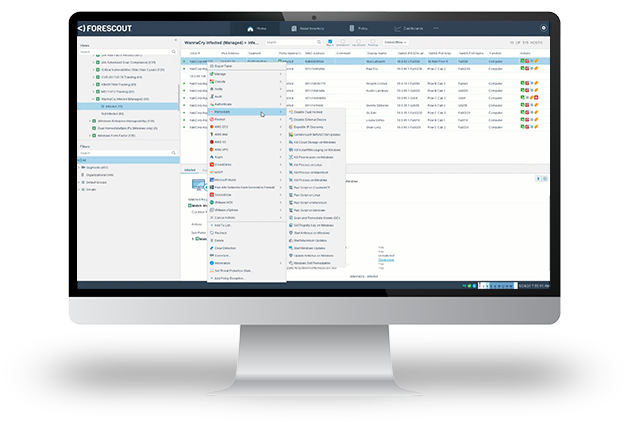
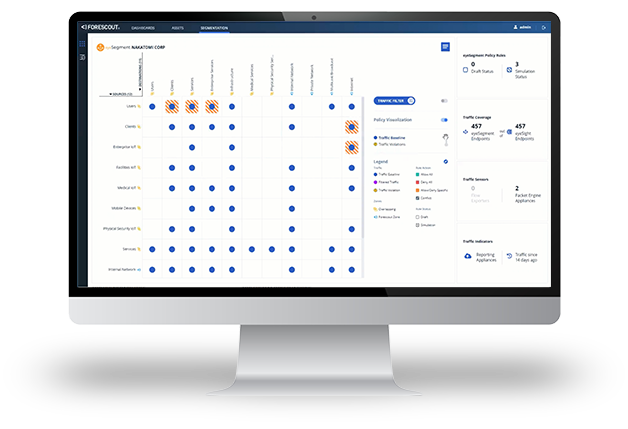
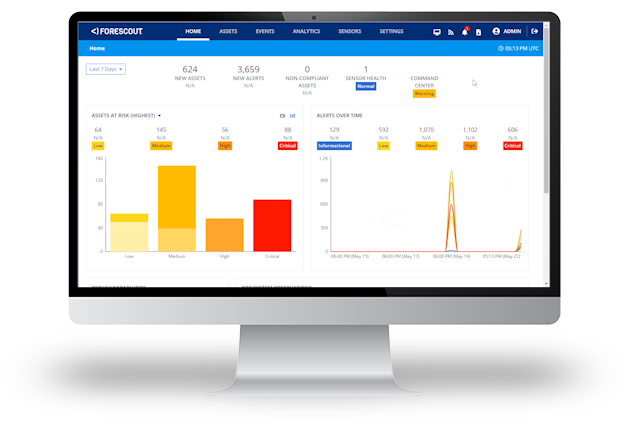
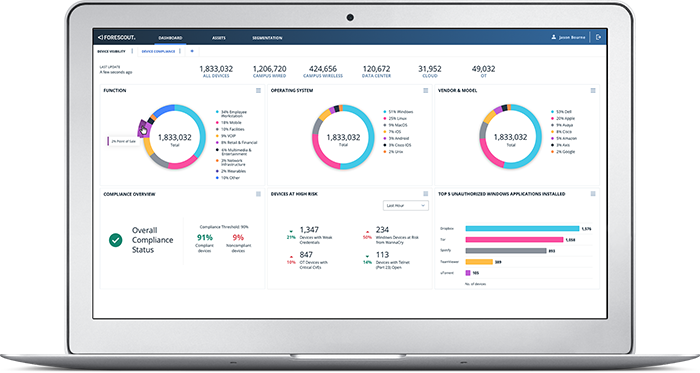
Customer Success with Asset Inventory
Learn More“Forescout showed us things that we didn’t know existed – mainly biomedical and environmental devices that were plugged into our network and talking out of the network as well.”
— CISO, major Florida medical center

Learn More“When we start enriching data from other tools with accurate, real-time data from Forescout, our cybersecurity team is able to make data-driven decisions with confidence. It allows me to sleep at night.”
— Bilal Khan, Chief Technology and Security Officer, NJ TRANSIT

Read More“When there is trust, there is speed. The Forescout platform is invaluable because it provides the level of visibility that gives us that trust – trust that we know exactly what devices are on our network, along with the situational awareness both to be proactive and to address issues as they arise.”
— Chief Technology Officer, U.S. State Government Agency