Hacktivists attack U.S. water treatment plant – analysis and implications
Almost a year ago to the day, on December 1 2022, Forescout Vedere Labs published a report detailing several hacktivist operations that targeted critical infrastructure in response to the Russian invasion of Ukraine and other geopolitical developments.
Since the most recent chapter in the Hamas-Israel conflict started on October 7, there have been multiple similar claims of attacks from hacktivists taking opposing sides in the conflict. However, most of these claims have gone unconfirmed or entirely debunked… Until now.
In this blog post, we examine a recent, confirmed attack by the anti-Israeli hacktivist group Cyber Aveng3rs. The attack targeted the municipal water authority of Aliquippa, Pennsylvania.
The attack
On November 25, the municipal water authority of Aliquippa confirmed that one of its booster stations – used to maintain water pressure and flow – was hacked, and fortunately, that there was no risk to the water supply. According to news outlets, the “compromised network also serviced several security cameras.” Spokespeople for the water authority stress that the attack triggered an alarm that subsequently disabled the system, which has since been manually operated. The water authority also shared an image of their compromised/defaced Human Machine Interface (HMI) – which is manufactured by the Israeli company Unitronics:

Figure 1 – Compromised HMI November 2023, from https://www.cbsnews.com/pittsburgh/news/municipal-water-authority-of-aliquippa-hacked-iranian-backed-cyber-group/
The image posted on the HMI screen appears quite similar to those of other defacement attacks against irrigation systems from the same manufacturer in Israel in April 2023:
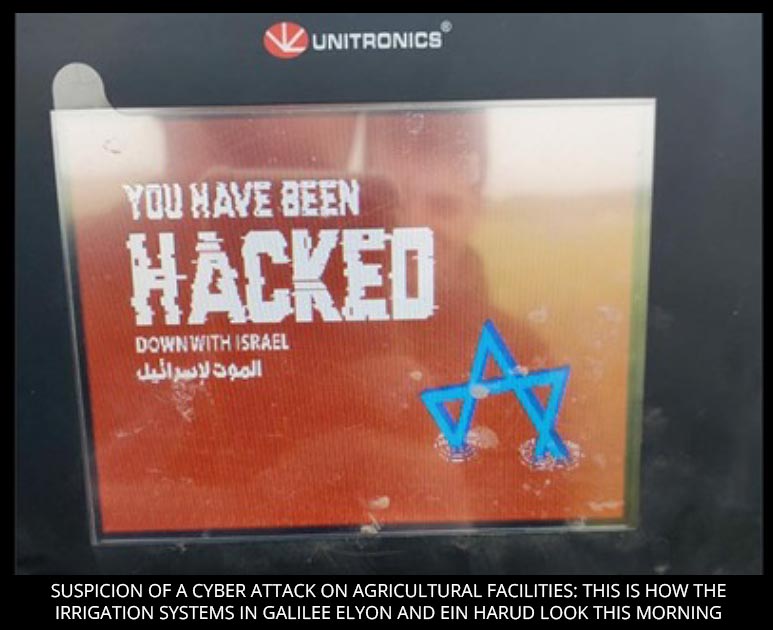
Figure 2 – Compromised HMI April, from https://www.jns.org/cyberattack-shutters-galilee-farm-water-controllers/
The two main differences between the attack images are the newer attack’s message about Israeli-made equipment and its addition of the logo of the Cyber Aveng3rs hacktivist group.
Taking full credit for the attack on November 26, the Cyber Aveng3rs posted on their X account and Telegram channel the following messages, Clearly stating that their attack scope has expanded (“EVERY EQUIPMENT MADE IN ISRAEL…”) and that more attacks can be expected (“the worst has just begun…”):
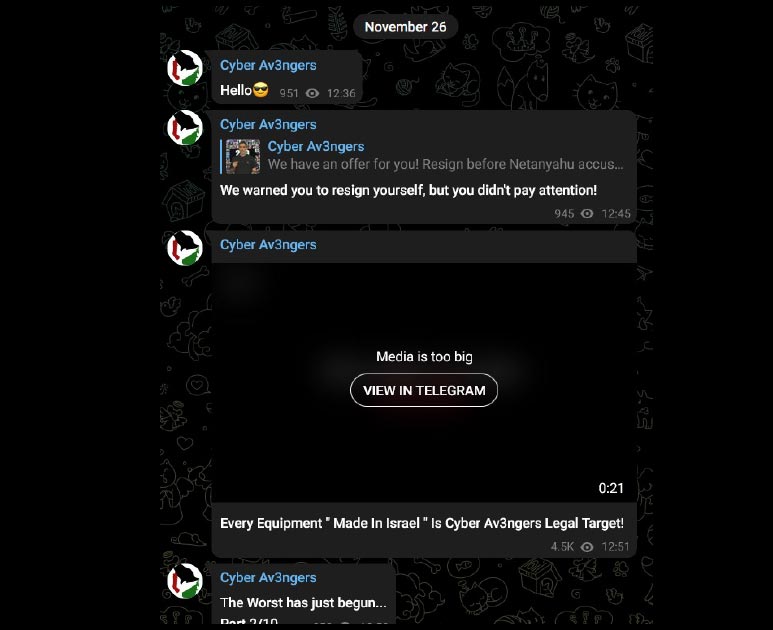
Figure 3 – Message of expanded attack scope posted to Telegram on November 26, 2023
Technical analysis
Currently, full details about the most recent attack are not publicly available. One of the main questions is, “How did the hacktivists managed to gain initial access to the HMI?” As with other water systems compromised in the past, this one was likely exposed directly to the Internet, although initial access could have also occurred via the “several security cameras” in the water authority’s network. On October 30, 2023, the same hacktivist group claimed attacks on several Israeli water treatment plants and released videos from their cameras, indicating some level of access to this type of equipment.
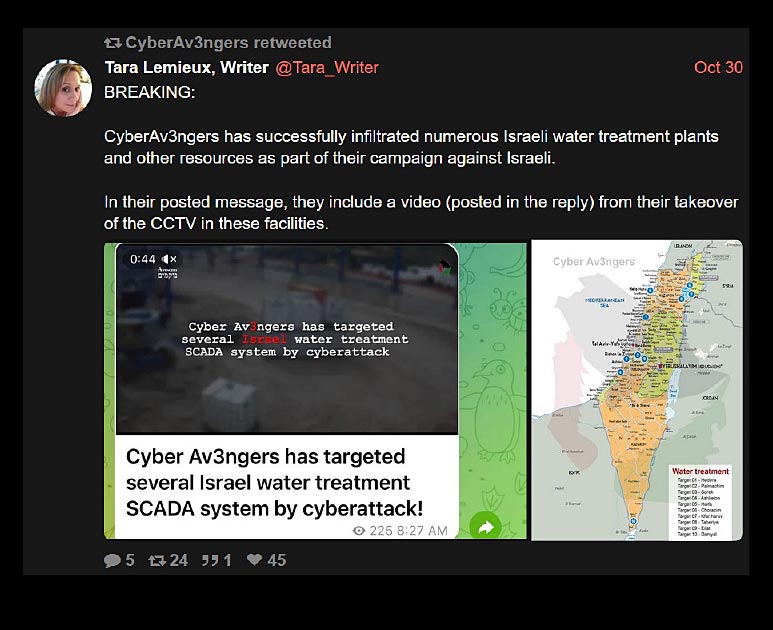
Figure 4 – October 30, 2023 Retweet of Cyber Av3ngers claim
The Unitronics V570 device shown in the image released by the water authority is a PLC+HMI combination. After gaining initial access to this system, it remains unclear how the attackers interacted with it to deface the HMI. Also unclear is what else they may have done, such as changing PLC settings or process variables.
The attackers could have defaced the HMI by downloading a new HMI graphic using the engineering software (VisiLogic, which is freely available). These devices also support an engineering protocol called PCOM, which allows users to change network settings of a device, set system registers or take many other actions. There have been Metasploit modules available for PCOM scanning and interaction since 2019 as well as an nmap script for fingerprinting Unitronics devices. This type of Metasploit module is a favorite tool within hacktivist arsenals, as it eliminates the need to develop custom malware, such as the malware used by state-sponsored actors. However, we cannot yet confirm which tool was used to interact with the compromised device.
Conclusion – other asset owners may be in danger
There are currently more than 1,800 Internet-exposed Unitronics PLCs in the world. Many of them are located in the US, some in major cities such as Chicago (52) and Dallas (14). Other regions with significant numbers of Unitronics PLCs include Australia, Europe and Singapore.
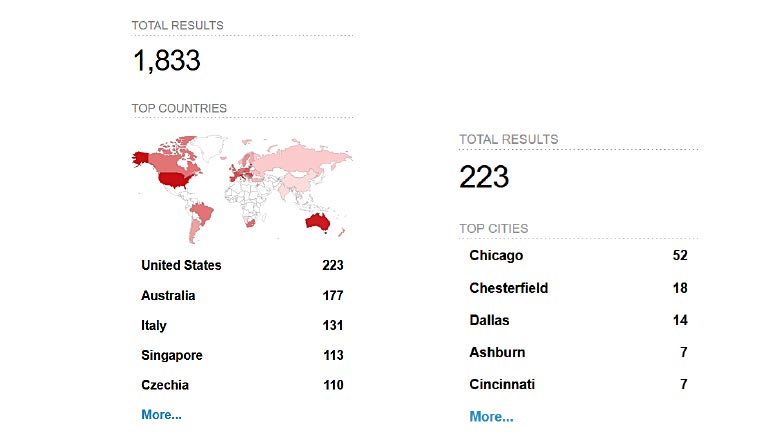
Not all of the Internet-exposed Unitronics PLCs run water treatment or even critical infrastructure. For instance, we see controllers for swimming pools and other private facilities. However, many of the devices are potentially connected to critical infrastructure, such as the three PLCs located in Australia and labelled “Water supply” (see below):
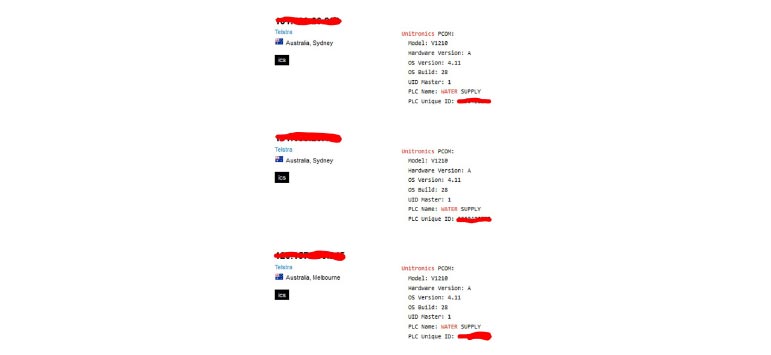
This attack represents a significant development in hacktivist tactics, and one that we expect to see replicated more widely.
Most hacktivists have previously restricted themselves to targets directly involved with, or located within, their target area. However, the statement published by the hacktivists that all equipment made in Israel is a Cyber Av3ngers legal target expands their target group significantly, and to an extent, poses a threat to inflict economic, as well as cyber damage on Israel.
We recommend that organizations that view themselves at risk of this attack conduct a through audit and risk assessment to enable them to take the appropriate steps to secure their infrastructure, regardless of where it has been manufactured.