Government and Financial Services hardest-hit by Windows CVE 2020-0601
Incident Response Updates:
- Jan. 14-15: Forescout security policies deployed across multiple public sector networks
- Jan. 15-16: Multiple PoC exploits published for CurveBall/ChainOfFools (Windows CVE-2020-0601)
- Jan. 16: Sample Forescout security policies shared and available via Forescout Community
- Download VR CryptoAPI in Forescout Security Policy Template (SPT) v20.0.01.
The NSA recently reported a widespread and dangerous Microsoft crypto security vulnerability. The negative consequences of Windows OS flaw CVE-2020-0601 are potentially devastating in the short and long-term. Successful exploitation could unravel our public use and trust of public key infrastructure (PKI) to deliver safe updates to fleets of Windows devices that rely on such updates to remain secure.
Forescout Research Labs taps Device Cloud data
To quantify the enterprise impact, Forescout Research Labs used data from the Forescout Device Cloud, the largest crowdsourced repository of device data. We validated data from 8 million devices in five key verticals: Government, Financial Services, Retail, Healthcare, and Manufacturing.
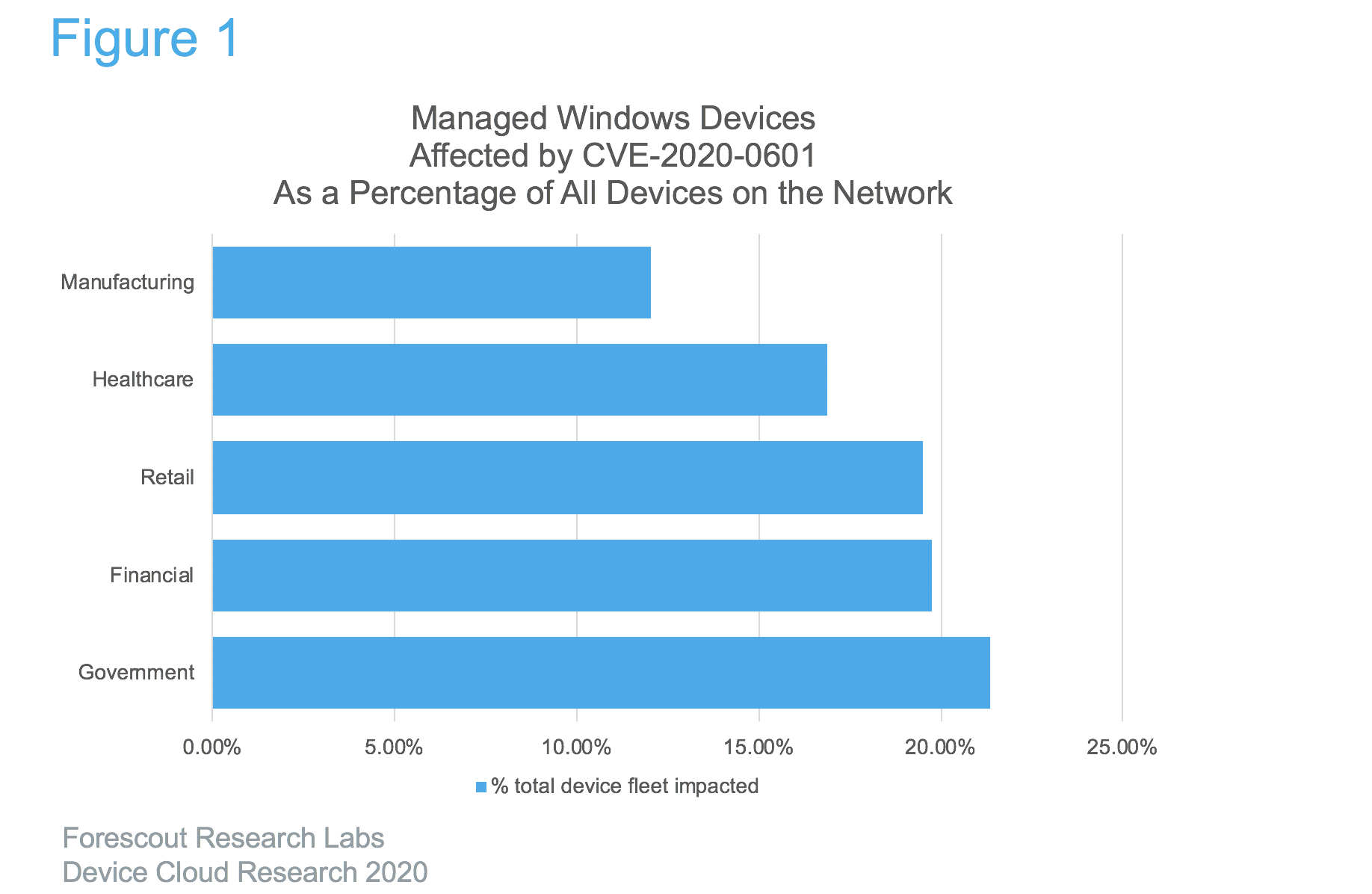
Government and Financial Services device fleets are the most impacted by the need to mitigate CVE-2020-0601.
What’s the impact?
The vulnerability is not reported as under active exploit, but it arrives at an interesting time, on the very day that masses of old Windows devices reach a rare end-of-support milestone: today, 14 January 2020.
Apply Device Control Fundamentals
1) Identify devices when they join the network – and don’t allow untrusted devices full access to enterprise resources and capabilities (Comply-to-Connect).
2) Continuously monitor the posture and configuration of devices on the network – and control non-compliant devices using segmentation and advanced orchestration (Continuous Diagnostics and Mitigation).
3) Ensure real-time asset inventory is what drives device-based control, and don’t rely on active scanners alone – especially in high-availability and OT environments where Windows automatic updates must be disabled.
Control Recommendations
Forescout eyeSight provides customers 100% device visibility to ensure detection of all unaddressed/unpatched Windows endpoints with a TLS certificate. With automation enabled, devices can be updated upon admission to the network and monitored continuously for their patch and security status. Federal customers utilizing Forescout through programs like Continuous Diagnostics and Mitigation (CDM) and Comply-to-Connect will be able to determine if this CVE is present on any devices and if the patch is applied correctly.
In addition to automated patching, further control actions available to Forescout customers include: delivering direct user notifications, enforcing device segmentation and quarantine, and scripting/anomaly detection.
Join the Forescout Community Discussion on how to control devices impacted by Windows CVE-2020-0601: