Exotic attacks are blurring the boundary between MRI/CT images, malware and life-threatening cancer research and diagnosis
Digital Imaging and Communications in Medicine (DICOM) is a 30-year-old standard for medical imaging exchange and storage that is prevalent in modern inpatient and acute trauma centers like hospitals, where expensive imaging equipment is common. Think of DICOM format like JPEG—it’s how medical images like x-rays are stored digitally. DICOM is at the center of two novel attack methods related to medical imaging that were exposed in April by healthcare cybersecurity experts. The first method was uncovered by a team of researchers from Ben-Gurion University who demonstrated how their deep learning code (CT-GAN) could alter MRI and CT scan machines by erasing real cancerous nodes or adding fake evidence of such. The video of the simulated scenario shows the red team deploying a rogue device in a hospital data closet (Raspberry Pi) that compromised the wireless network using a two-year-old KRACK vulnerability. The team then moved laterally to the server storing images and maliciously altered life-critical patient data stored in DICOM format. The second method was recently published by another research team at Cylera Labs and allows an attacker to easily hide malware inside MRI and CT scan images. The potential impact of these two new findings on healthcare delivery organizations (HDOs) also extends to the Picture Archiving and Communication System (PACS) that stores the images.
Suddenly, protected medical records might come with malware attached, in a mind-boggling recipe where malware can’t simply be uploaded and checked against forensics and threat intel resources in the cloud-like VirusTotal because that would be a breach of the associated HIPAA-protected personal health information (PHI). Deepfaked cancer images have fooled professional doctors and can force unnecessary, expensive and life-threatening operations or as the researchers state: “An attacker may perform this action in order to stop a political candidate, sabotage research, commit insurance fraud, perform an act of terrorism or even commit murder.”
When our researchers threat modeled the above attack vectors and complex “kill chain” paths of the attack scenarios, we even envisioned the possibility of merging several distinct attacks, where the malware Portable Executable (PE) embedded in the DICOM image could propagate as a network worm with a payload of the CT-GAN malware necessary to carry out the cancer deep-fake attack. Such a complex attack might seem improbable, but attackers are getting increasingly creative and attacks are getting more physical.
How do these DICOM medical imaging attacks work?
Each DICOM .dcm image file has a header for describing the file contents. Unfortunately, the original DICOM spec allows a header that’s too open—the header format is simply not strict enough and it has enough padding to add unintended Windows PE code that escapes from the data context of the image. The resulting mutant is a hybrid file—it’s both a functioning DICOM image and a functioning Windows PE. The underlying issue is that some versions of Microsoft Windows allow non-executable files to be run from the command prompt if the file header looks like a Windows executable.
This tactic isn’t exactly new in healthcare cybersecurity. For example, it’s widely understood that images can even have live scripting code (e.g., PHP) that can be executed on a web server that’s parsing and processing the image data stream—escaping from this data context is what injection is all about. The underlying issue is that writing parsers is hard and there have been major issues in parsers of all image types including PNG, JPG, GIF, and TIFF across many languages and vendor products. Related, the fascinating field of steganography—hiding data in images, not seen to the human eye—has been around since the beginning of the digital file format age.
Malware that lives in HIPAA-protected neighborhoods
What’s particularly interesting is that this DICOM malware resides in the protected garden of HIPAA-regulated data stores. That makes the discussion of this malware even more entangling than a discussion of zero-day PDF exploits or advanced industrial AutoCAD malware.
Researching DICOM in Forescout Device Cloud
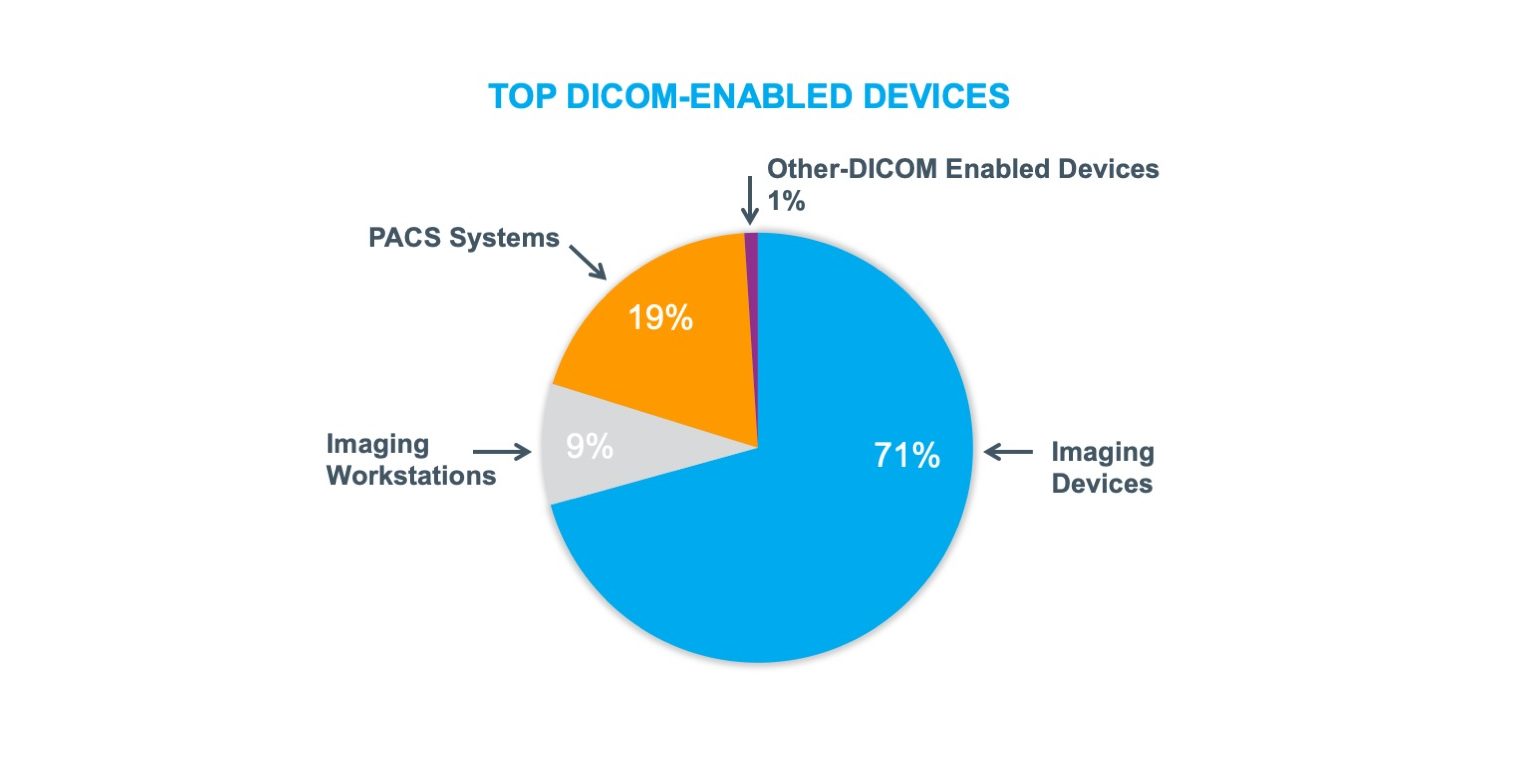
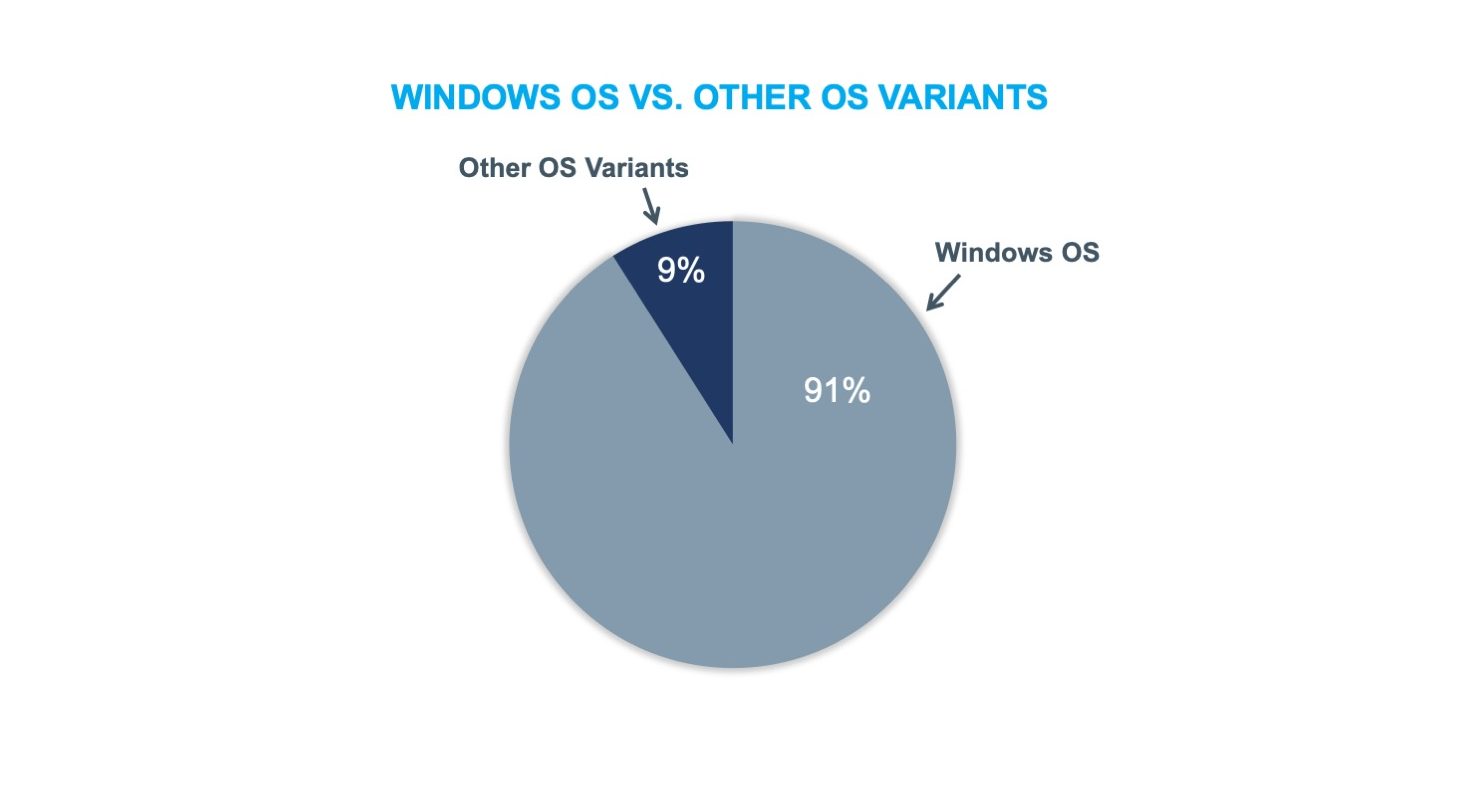
The Forescout platform provides device visibility and automated control to effectively manage cyber, operational and compliance risks in healthcare cybersecurity while increasing security operations productivity. To better understand the context and kinds of devices impacted, Forescout researchers referenced the Forescout Device Cloud to determine the kinds of top DICOM-enabled devices and better understand the nature of Windows versus non-Windows in DICOM and PACS environments. We researched more than 2,000 DICOM-related devices to draw our conclusions.
What we found was that nearly three-quarters of the devices were categorized as imaging devices, and the majority of the remainder consisted of PACS systems and imaging workstations. Unsurprisingly, we also found that that most of the devices were running a Windows Operating System (OS).
Mitigations and best practices for securing DICOM devices
Any connected medical devices, especially DICOM, must be segmented and monitored, updated with Antivirus (A/V) and Endpoint Detection and Response (EDR) and eventually upgraded as the DICOM protocol is redesigned or hardened. Encrypting DICOM using TLS is the current best practice but may prove difficult and disruptive to deploy and manage. Encryption of DICOM in transit is not enough to prevent the attack if the malware can be delivered through other means such as email or a USB drive.
One common issue in healthcare cybersecurity is that most Human Machine Interfaces (HMIs) are Windows workstations that are monitoring and controlling medical devices. These workstations are often behind in updates and are shared by many users that potentially abuse corporate policies (e.g., checking personal email, browsing social media), opening the doors to the inadvertent introduction of malware to the internal network.
In the case of the CT-GAN scenario, prior to the image manipulation attack there may be warning signs from the rogue devices introduced to the network. Forescout Rogue Device Detection can alert administrators to take action on spoofed MAC attempts. Wireless network hygiene can prevent attackers from passively snooping from a nearby location. To help mitigate the wireless KRACK vulnerability, we released a custom detection last year, SPT VR KRACK.
Those responsible for securing connected medical devices and HDO networks should carefully consider lateral movement attacker opportunities, especially for Windows devices, and leverage the MITRE ATT&CK framework to discuss Exploitation of Remote Services (e.g., remote desktop protocol (RDP)) and Windows Admin Shares (e.g., SMB). In particular, SMB has been in the spotlight with WannaCry attacks and the Orangeworm Group targeting Healthcare.

Forescout customers can create custom technical policies to detect devices that communicate with the DICOM protocol. The following are classification checks for the presence of DICOM Application Entity fields or DICOM Implementation Class UID fields:
In theory, it may be technically possible to parse DICOM traffic, extract the potentially infected image and then either attempt to run it in a sandboxed environment or check its hash against known threat intelligence sources, but the attacks Cylera describes actually do not mention malicious DICOM data in transit. The only proof of concept #3 propagates, but it does so using a common Windows weakness: SMB. In the case of CT-GAN, the malware can be delivered via many network avenues that should be monitored by intrusion prevention.
This approach for healthcare cybersecurity is valuable for post-incident forensic analysis but not viable for securing a real network with large image throughput. Protection from this kind of attack can still be achieved using traditional Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) for detecting typical malware patterns such as C2C communications and exploitations of known vulnerabilities for beaconing. These patterns are likely to be leveraged especially in the healthcare domain where the main attacker goal is often data exfiltration (e.g., C2C) and the IT infrastructure is known to have unpatched vulnerabilities. Some of these capabilities are available within the Forescout platform thanks to its recent acquisition and integration of the powerful SilentDefense OT monitoring solution.
