A Four Step Guide to Secure Your ICS Network Using ISA 99/IEC 62443
Our guide on the components of IEC 62443 and how to easily implement the standard into your ICS network.
IEC 62443, formerly known as ISA 99, is the global standard for the security of Industrial Control System (ICS) networks and helps organizations to reduce both the risk of failure and exposure of ICS networks to cyberthreats. This standard was produced by the International Society of Automation (ISA) and has been taken over by the International Electrotechnical Commission for further development. The framework of this standard guides operators of ICS networks through requirements, controls and best practices necessary for a secure industrial network.
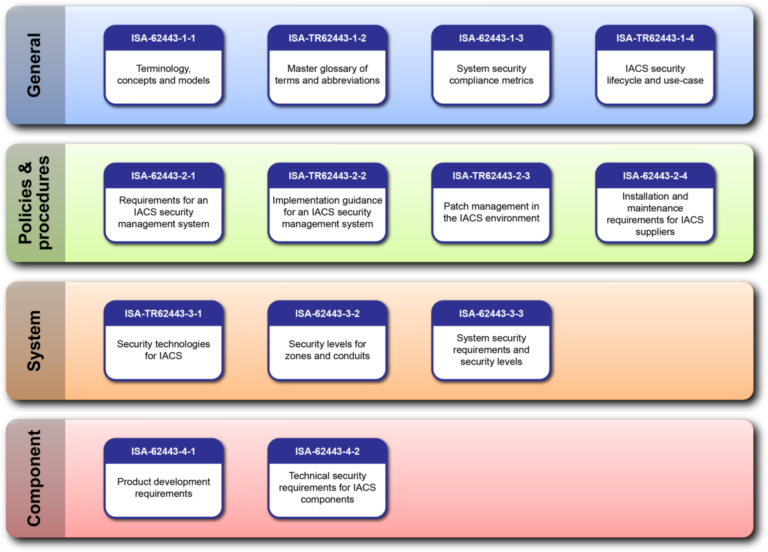
The Structure and Documents of the IEC 62443 Standard
IEC 62443 consists of thirteen documents which are organized into four groups: General, Policies and Procedures, System, and Component. The first two groups describe concepts, uses cases, policies and procedures associated with ICS security, whereas the two latter groups, System and Component, define the technical requirements for networks and system components. We will take a closer look at these two sections of the standard below.
System Requirements
The three documents within the System group concern the design choices, modifications or adjustments required to enhance the security of an ICS network.
The first document (IEC 62443-3-1) provides an overview of existing network security technologies, their advantages and limitations.
The second (IEC 622443-3-2) addresses security risk assessment and network design. It suggests how organizations should segment their network into zones and conduits, grouping systems which are similar in functionality and restricting access to limit threat exposure and propagation.
Finally, the third document (IEC 62443-3-3) describes general system security requirements such as authentication, data confidentiality and system integrity, emphasizing that performance and availability should not be compromised during the process of addressing these requirements.
Component Requirements
The Component group consists of two documents. The first (IEC 62443-4-1) deals with a development process for ICS products, aimed at reducing the number of security vulnerabilities in control system solutions. The second document (IEC 62443-4-2) specifies the technical requirements for securing the individual components of an ICS network.
Based on the requirements in the System and Components groups, we can identify four steps that industrial operators should follow to enhance the security of their ICS network and successfully implement IEC 62443:
- Data Gathering
You cannot properly secure your network if you do not know what it is that needs securing. Gathering accurate asset information, including details on how they communicate and how your network operates, is a fundamental first step to enhance its security. - Network Security Assessment
This step involves analyzing the results of step one and assessing your network’s current state of security. This will allow you to determine the best strategy for applying required modifications or adjustments. - Solution Build
Step three leverages the criticalities and priorities identified in step 2 and prepares the network for the implementation of the required countermeasures. This includes the definition of procedures, the identification and separation of the network into zones and the definition of conduits (i.e., communication flows). - Solution Deployment
The final step in securing your network is to deploy the chosen countermeasures, which could, for instance, be represented by segmentation and monitoring technology. These measures need to be integrated into daily operation to maintain the security of your network and its processes.
To ensure the success of IEC 62443, it is important to systematically work through the four steps above. Without complete and accurate data and assessments, and without implementing solutions built around well-defined procedures, a successful outcome cannot be guaranteed, and the network may remain inadequately protected from threats.
If you would like to know more about IEC 62443 and how you can apply it to your ICS network easily with our solution, download this eBook.
