See it. Secure it. Assure it.
Continuously identify, protect and ensure
the compliance of all cyber assets across your organization.

Risk and Exposure Management
Identify, quantify and prioritize cybersecurity risk and compliance
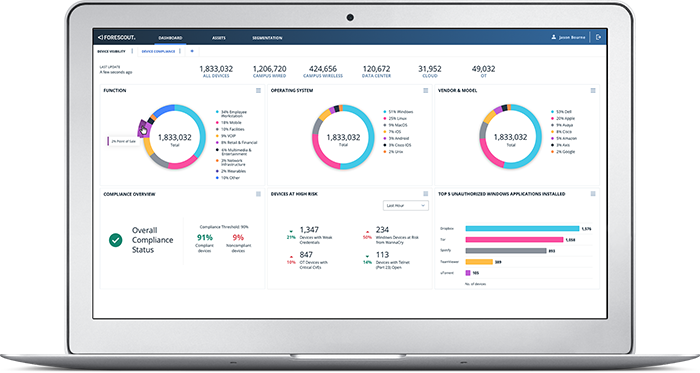
- Cyber asset management
- Visibility & compliance
- Risk prioritization

Network Security
Assess, segment and enforce with proactive and reactive controls
- Network asset control
- Risk & threat containment
- Segmentation management
The Forescout Advantage
The only automated cybersecurity company that continuously identifies, protects and ensures the compliance of all managed and unmanaged assets – IT, IoT, IoMT and OT – so you can more effectively manage cyber risk and mitigate threats.
Vendor & Device Agnostic
Real-Time & Continuous
Managed & Unmanaged Cyber Assets
Flexible Deployment
Converged Platform
Proven at Scale
Better Safe Than Sorry
Our research takes a fresh look at the topic of exposed OT/ICS by examining the nuanced evolution of exposed devices from 2017 to 2024. Read the full report to see other findings such as:
- Why many of these internet-exposed OT devices and protocols appear to be the result of system integrator practices
- How exposure rates can be reduced proactively through targeted notification efforts
- Specific statistics about Unitronics PLCs and devices running InterNiche and Nucleus TCP/IP stacks
Customer Confidence
66M+
Devices Protected
39B+
Unique Data Points Monitored
23+
Years in Business
3000+
Customers Globally
Latest from Forescout
The Emergence of Exposed ICS: Trends, Threats, and Best Practices
WEBINAR The Emergence of Exposed ICS: Trends, Threats, and Best Practices Despite years of efforts to raise awareness, implement regulations, and issue advisories, operational technology (OT) and industrial control systems (ICS) continue to face significant exposure risks. Since 2017, Forescout Research – Vedere Labs has diligently monitored these risks, uncovering…
Read More
Analyst Report
2023 Gartner® Market Guide for Operational Technology Security
A holistic assessment by Gartner of the current state of this changing market to help future-proof your OT cybersecurity strategy.
Access
Blog
The Chinese Communist Party’s Threat to US Critical Infrastructure
Against the backdrop of global tensions in Israel, Ukraine, and the South China Sea, US officials testified before Congress that they disrupted a serious Chinese cyberattack aimed at embedding malware within the nation’s critical infrastructure. At the heart of this revelation is a botnet compromising hundreds of…
Read MoreSchedule a Demo
Get a personalized tour of our solutions and see how we can help you automate cybersecurity.