OT:ICEFALL: 56 Vulnerabilities Caused by Insecure-by-Design Practices in OT
After the publication of the original OT:ICEFALL report, and several subsequent updates, Forescout Vedere Labs has published a follow up conclusion report. Read the related blog post
After the publication of the original OT:ICEFALL report, Forescout Vedere Labs identified and disclosed three new vulnerabilities affecting OT products from two German vendors: Festo automation controllers and the CODESYS runtime, which is used by hundreds of device manufacturers in different industrial sectors, including Festo. Read the related blog post
It has been 10 years since Project Basecamp, a research project conducted by Digital Bond that investigated how critical operational technology (OT) devices and protocols were, to use the term they coined, “insecure by design.” Since then, we have seen hugely impactful real-world OT malware such as Industroyer, TRITON, Industroyer2 and INCONTROLLER abusing insecure-by-design functionality.
In collaboration with CISA’s vulnerability disclosure process, Forescout’s Vedere Labs today is disclosing OT:ICEFALL, a set of 56 vulnerabilities affecting devices from 10 OT vendors. Why “Icefall”? That’s the name of the second stop on the Everest route, after Base Camp, and given the rising number of OT vulnerability disclosures, we know we have a mountain to climb to secure these devices and protocols.
The vulnerabilities in OT:ICEFALL are divided into four main categories:
- Insecure engineering protocols
- Weak cryptography or broken authentication schemes
- Insecure firmware updates
- Remote code execution via native functionality
Devices affected by OT:ICEFALL
The table below shows the devices affected by OT:ICEFALL. More details about each vulnerability are available in our technical report. We also recommend readers follow the advisories of each vendor for more details on specific impact and products affected by each vulnerability.
| Manufacturer | Model | Device type |
|---|---|---|
| Bently Nevada | 3700, TDI equipment | Condition monitors |
| Emerson | DeltaV | Distributed control system |
| Emerson | Ovation | Distributed control system |
| Emerson | OpenBSI | Engineering Workstation |
| Emerson | ControlWave, BB 33xx, ROC | Remote terminal unit |
| Emerson | Fanuc, PACsystems | Programmable logic controller |
| Honeywell | Trend IQ* | Building controller |
| Honeywell | Safety Manager FSC | Safety instrumented system |
| Honeywell | Experion LX | Distributed control system |
| Honeywell | ControlEdge | Remote terminal unit |
| Honeywell | Saia Burgess PCD | Programmable logic controller |
| JTEKT | Toyopuc | Programmable logic controller |
| Motorola | MOSCAD, ACE IP gateway | Remote terminal unit |
| Motorola | MDLC | Protocol |
| Motorola | ACE1000 | Remote terminal unit |
| Motorola | MOSCAD Toolbox STS | Engineering workstation |
| Omron | SYSMAC Cx series, Nx series | Programmable logic controller |
| Phoenix Contact | ProConOS | Logic runtime |
| Siemens | WinCC OA | Supervisory control and data acquisition (SCADA) |
| Yokogawa | STARDOM | Programmable logic controller |
There are four vulnerabilities affecting one vendor still under disclosure. We do not give details about them but include them in our quantitative analysis on the technical report.
OT:ICEFALL vulnerability categories
Although the impact of each vulnerability is highly dependent on the functionality each device offers, they fall under the following categories:
- Remote code execution (RCE): Allows an attacker to execute arbitrary code on the impacted device, but the code may be executed in different specialized processors and different contexts within a processor, so an RCE does not always mean full control of a device. This is usually achieved via insecure firmware/logic update functions that allow the attacker to supply arbitrary code.
- Denial of service (DoS): Allows an attacker to either take a device completely offline or to prevent access to some function.
- File/firmware/configuration manipulation: Allows an attacker to change important aspects of a device such as files stored within it, the firmware running on it or its specific configurations. This is usually achieved via critical functions lacking the proper authentication/authorization or integrity checking that would prevent attackers from tampering with the device.
- Compromise of credentials: Allows an attacker to obtain credentials to device functions, usually either because they are stored or transmitted insecurely.
- Authentication bypass: Allows an attacker to bypass existing authentication functions and invoke desired functionality on the target device.
Abusing these types of insecure-by-design, native capabilities of OT equipment is the preferred modus operandi of real-world industrial control system (ICS) attackers (see, for instance, Industroyer2 and INCONTROLLER). These vulnerabilities, and the proven desire for attackers to exploit them, demonstrate the need for robust, OT-aware network monitoring and deep-packet-inspection (DPI) capabilities.
Why this research matters
With OT:ICEFALL, we wanted to disclose and provide a quantitative overview of OT insecure-by-design vulnerabilities rather than rely on the periodic bursts of CVEs for a single product or a small set of public, real-world incidents that are often brushed off as a particular vendor or asset owner being at fault. These issues range from persistent insecure-by-design practices in security-certified products to subpar attempts to move away from them. The goal is to illustrate how the opaque and proprietary nature of these systems, the suboptimal vulnerability management surrounding them and the often-false sense of security offered by certifications significantly complicate OT risk management efforts. Some of the main findings of this research include:
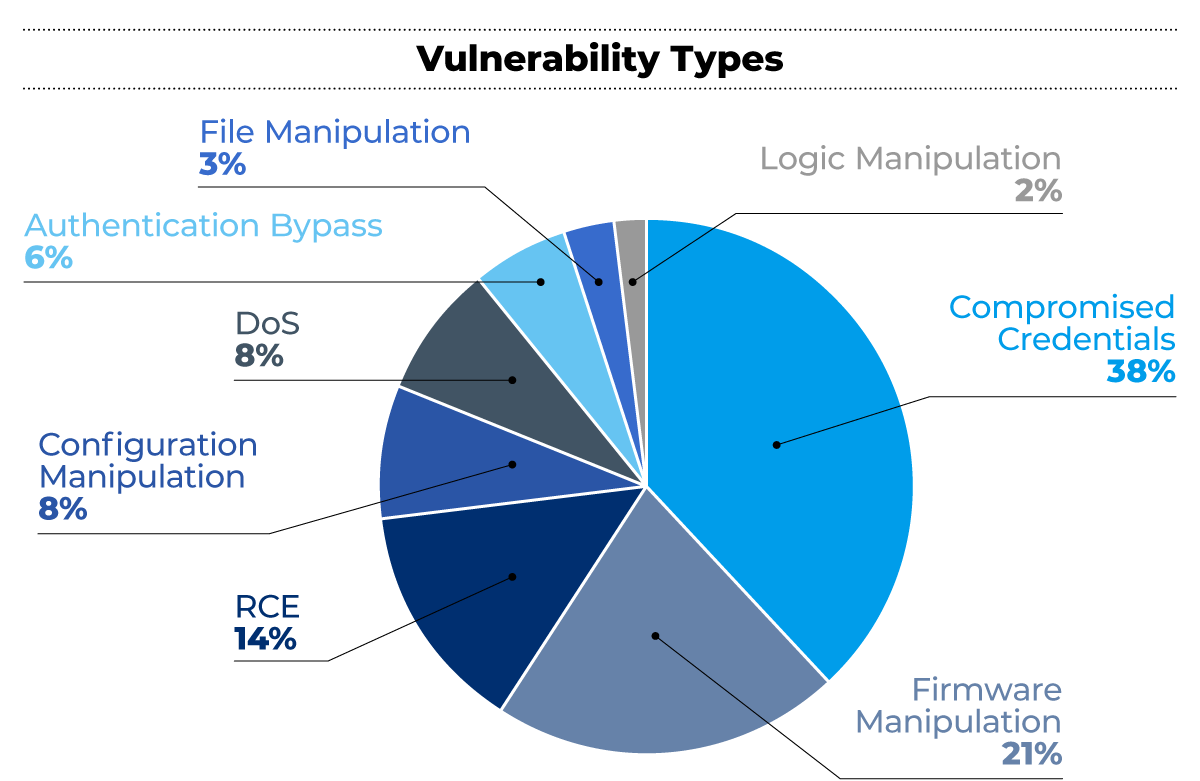
- Insecure-by-design vulnerabilities abound: More than a third of the vulnerabilities we found (38%) allow for compromise of credentials, with firmware manipulation coming in second (21%) and remote code execution coming third (14%). The prime examples of insecure-by-design issues are the nine vulnerabilities related to unauthenticated protocols, but we also found many broken authentication schemes, which demonstrates subpar security controls when they are implemented.
- Vulnerable products are often certified: 74% of the product families affected by OT:ICEFALL have some form of security certification and most issues we report should be discovered relatively quickly during in-depth vulnerability discovery. Factors contributing to this problem include limited scope for evaluations, opaque security definitions and focus on functional testing.
- Risk management is complicated by the lack of CVEs: It is not enough to know that a device or protocol is insecure. To make informed risk management decisions, asset owners need to know how these components are insecure. Issues considered the result of insecurity by design have not always been assigned CVEs, so they often remain less visible and actionable than they ought to be.
- There are insecure-by-design supply chain components: Vulnerabilities in OT supply chain components tend to not be reported by every affected manufacturer, which contributes to the difficulties of risk management.
- Not all insecure designs are created equal: We investigate three main pathways to gaining RCE on level 1 devices via native functionality: logic downloads, firmware updates and memory read/write operations. None of the systems analyzed support logic signing and most (52%) compile their logic to native machine code. 62% of those systems accept firmware downloads via Ethernet, while only 51% have authentication for this functionality.
- Offensive capabilities are more feasible to develop than often imagined: Reverse engineering a single proprietary protocol took between 1 day and 2 man-weeks, while achieving the same for complex, multi-protocol systems took 5 to 6 man-months. This shows that basic offensive cyber capabilities leading to the development of OT-focused malware or cyberattacks could be developed by a small but skilled team at a reasonable cost.
Impact analysis
We estimate the impact of OT:ICEFALL based on the evidence collected during our research, using three main sources:
- Open-source intelligence: We looked at product documentation, datasheets and marketing information that mention where devices are used and their certification security status.
- We found that the products affected by OT:ICEFALL are known to be prevalent in industries such as oil and gas, chemical, nuclear, power generation and distribution, manufacturing, water treatment and distribution, mining, and building automation. We also found that many of these products are sold as “secure by design” or have been certified with OT security standards.
- Shodan queries: Shodan is a search engine that allows users to look for devices connected to the internet. Estimating the number of affected devices based on public data is difficult because these devices are not supposed to be accessible via the internet.
- We were able to see more than 5,000 of the affected devices exposed online via Shodan. Most of these are Saia Burgess and OMRON controllers or devices running the ProConOS runtime.
- Forescout Device Cloud: Forescout Device Cloud is a repository of information on 18+ million devices monitored by Forescout appliances present in customer networks.
- We queried Device Cloud for the vulnerable devices and found close to 30,000 results. The figure below shows the sectors in which the affected devices are most popular. Manufacturing is at the top with almost a third of observed devices. After that, we see healthcare, retail and government, mainly because of the presence of building automation controllers since these are industries with many large facilities. We see only a small presence in the OT-intensive oil and gas and utilities sectors, but that is likely because many of those types of customers do not share device information with Forescout’s Device Cloud.
Mitigation recommendations
Complete protection against OT:ICEFALL requires that vendors address these fundamental issues with changes in device firmware and supported protocols and that asset owners apply the changes (patches) in their own networks.
Realistically, that process will take a very long time. In addition to network monitoring, mitigations for OT:ICEFALL include isolating OT/ICS networks from corporate networks and the internet, limiting network connections to only specifically allowed engineering workstations and focusing on consequence reduction where possible. Below, we briefly discuss the most important mitigation strategies for asset owners:
- Discover and inventory vulnerable devices: Network visibility solutions enable discovery of vulnerable devices in the network and apply proper control and mitigation actions.
- Enforce segmentation controls and proper network hygiene to mitigate the risk from vulnerable devices. Restrict external communication paths and isolate or contain vulnerable devices in zones as a mitigating control if they cannot be patched or until they can be patched.
- Monitor progressive patches released by affected device vendors and devise a remediation plan for your vulnerable asset inventory, balancing business risk and business continuity requirements.
- Monitor all network traffic for malicious packets that try to exploit insecure-by-design functionality. You should block anomalous traffic, or at least alert its presence to network operators.
Further general recommended mitigation is available on CISA’s Shields Up initiative that includes a publication, Securing Industrial Control Systems, and list of recommended practices. Specific mitigation for each vulnerable device will be provided by the respective vendors.
How Forescout can help
Implementing mitigation for these vulnerabilities requires extensive visibility and segmentation of OT assets in a network. The Forescout Continuum Platform helps to achieve that via:
- Unparalleled insight into your entire device landscape without disrupting critical business processes. After discovering connected devices, Forescout auto-classifies and assesses those devices against company policies. The powerful combination of these three capabilities—discovery, classification and assessment — delivers the device visibility to drive appropriate policies and action.
- In-depth visibility and cyber resilience with both asset and communications inventory based on DPI. This allows for network monitoring and threat hunting capabilities, including threat and vulnerability indicators. Forescout’s eyeInspect product has native monitoring capabilities for the protocols used by the affected devices. New vulnerabilities are continuously added to the database that is released to customers every month.
- Accelerated design, planning and deployment of dynamic network segmentation across the extended enterprise to reduce your attack surface and regulatory risk. Forescout’s eyeSegment product simplifies the process of creating context-aware segmentation policies and allows visualization and simulation of policies prior to enforcement for proactive fine-tuning and validation.
- Sharing device context between the Forescout Continuum and other IT and security products to automate policy enforcement across disparate solutions and accelerate system-wide response to mitigate risks.
In addition to reading the technical report, watch the webinar with researchers for more information about OT:ICEFALL.